Advanced Security Logger By Pentest7
| 开发者 | Pentest7 |
|---|---|
| 更新时间 | 2021年10月27日 03:54 |
| PHP版本: | 5.4 及以上 |
| WordPress版本: | 5.8.1 |
| 版权: | GPLv2 or later |
| 版权网址: | 版权信息 |
详情介绍:
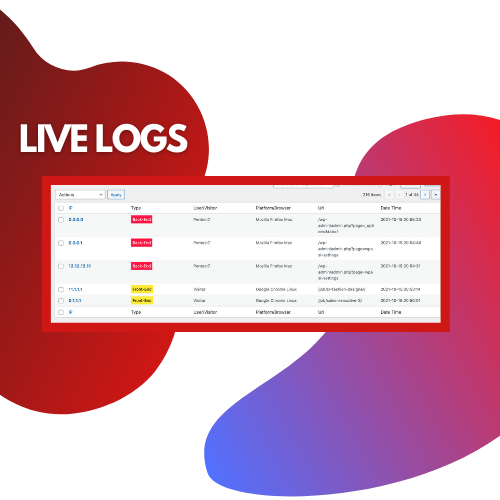
Advanced security logger comes with multiple different security features. It allows you to look at live logs of your website and lets you detect malicious activities of both users and admins. There are multiple security features of this plugin that you can explore. You can also hide your WordPress with this security plugin.
Features of Advanced Security Logger
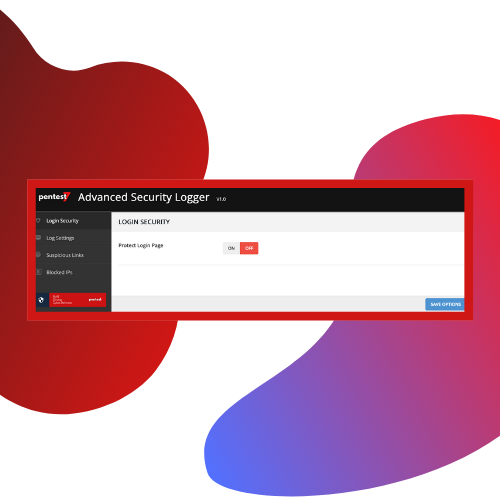
- Hide WordPress Login
- Advanced Log System
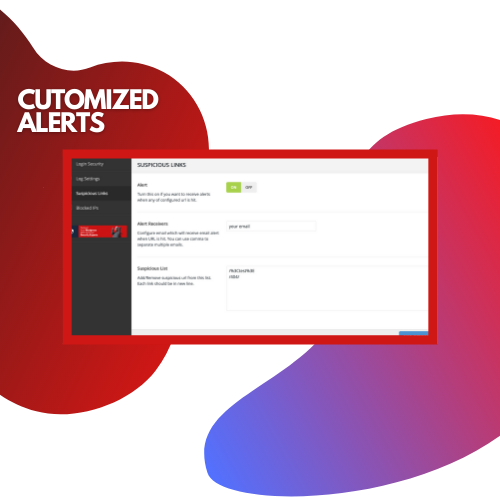
- Alert Feature
- All provided payloads should be URL encoded
- Block IPs
安装:
This section describes how to install the plugin and get it working.
e.g.
- Upload the plugin files to the
/wp-content/plugins/plugin-namedirectory, or install the plugin through the WordPress plugins screen directly. - Activate the plugin through the 'Plugins' screen in WordPress
- Use the Settings->Plugin Name screen to configure the plugin
- (Make your instructions match the desired user flow for activating and installing your plugin. Include any steps that might be needed for explanatory purposes)
屏幕截图:
常见问题:
Is this plugin FREE?
Yes, the plugin is 100% free.
What is penetration testing and how do i get it?
A penetration test, also known as a pen test or ethical hacking, is a cybersecurity approach that allows companies to uncover, test, and highlight security flaws. Know more at- https://blog.pentest7.io/what-is-penetration-testing-or-pentesting/
I have found a bug in your plugin, What to do?
Please contact us as soon as possible at hello@pentest7.io , We will try to patch the issue.