Counterespionage Firewall
| 开发者 | floodspark |
|---|---|
| 更新时间 | 2022年7月19日 13:46 |
| 捐献地址: | 去捐款 |
| PHP版本: | 7.0.33 及以上 |
| WordPress版本: | 6.0.1 |
| 版权: | GPLv2 or later |
| 版权网址: | 版权信息 |
详情介绍:
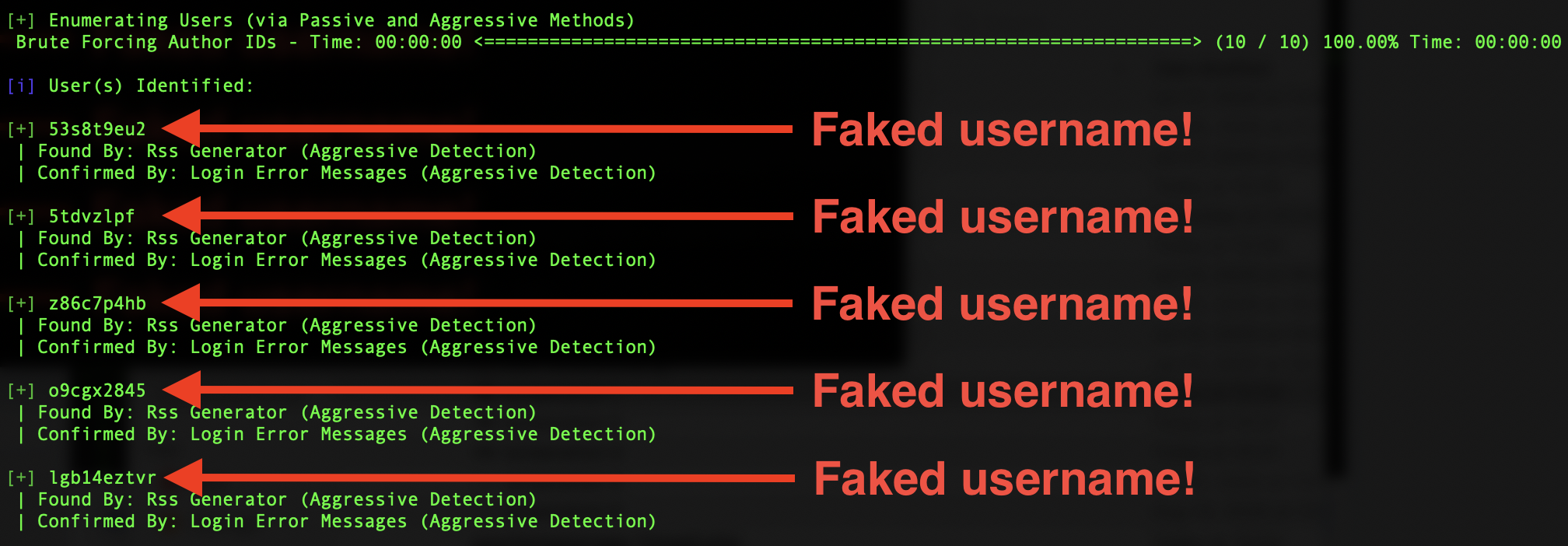
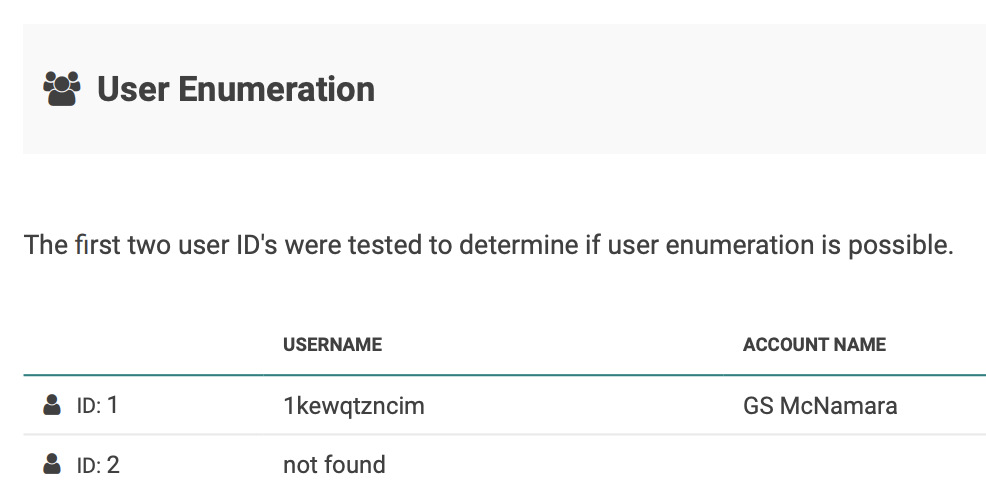
- Fake out WPScan and bots by hiding your real usernames, instead supplying them with fake ones they will never be able to log in with.
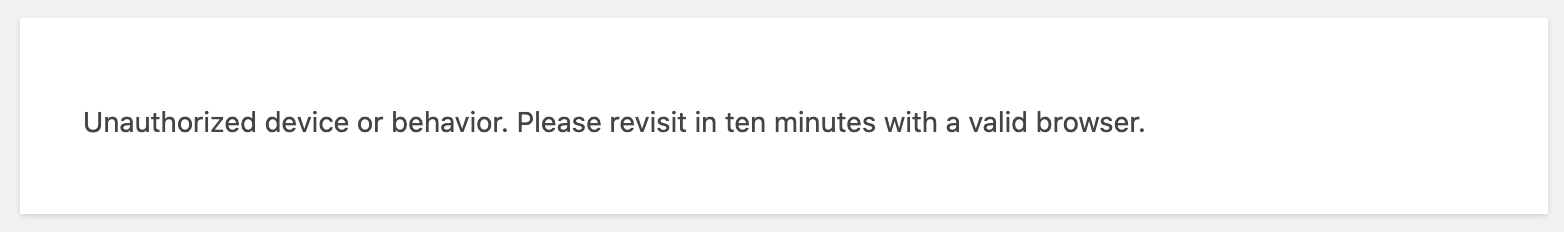
- Prevent bots from logging in even with your real password.
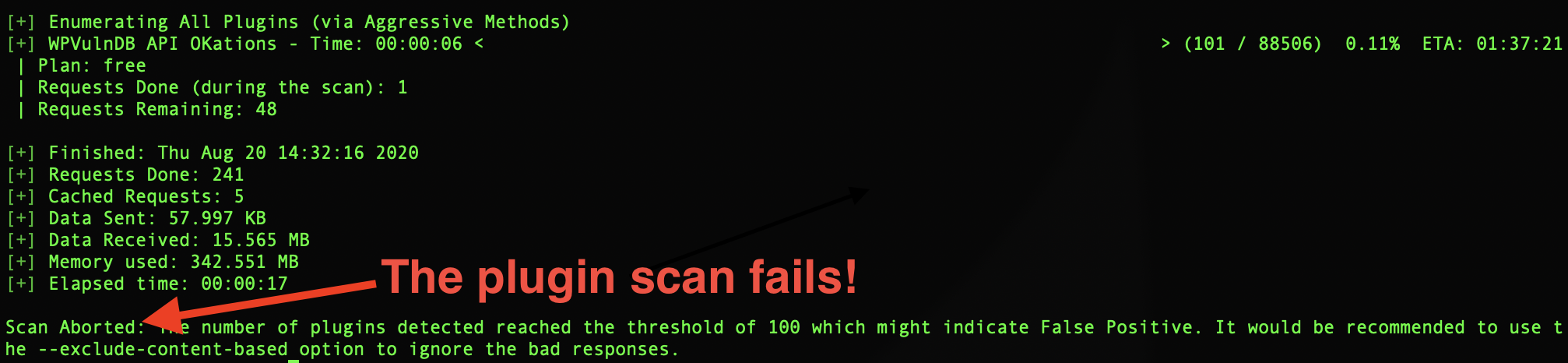
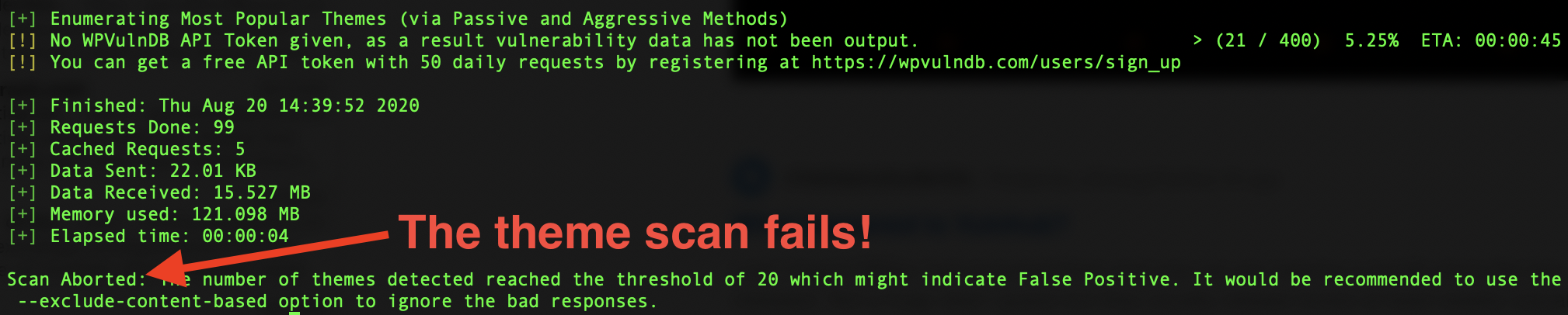
- Defeat WPScan's aggressive plugin and theme scans, also causing the scanner to terminate. ...as well as detect:
- Tor browser, with minor delay
- Chrome Incognito, with minor delay, over HTTPS
- Firefox Private Browsing, with minor delay
- Chrome-Selenium in its default configuration, with minor delay
- cURL in its default configuration
- Wget in its default configuration
- HTTP methods other than GET, POST, and HEAD
- Proxy probing
屏幕截图:
常见问题:
How can I test CEF's protection?
Use the Docker version of WPScan and the commands below. When prompted whether to update the database, you shouldn't need to.
- To verify that CEF deceives WPScan's username scan, issue the following command: docker run -it --rm wpscanteam/wpscan --url http://[yourbloghere.com] --enumerate u
- To verify that CEF deceives WPScan's plugin scan, issue the following command: docker run -it --rm wpscanteam/wpscan --url http://[yourbloghere.com] --plugins-detection aggressive
- To verify that CEF deceives WPScan's theme scan, issue the following command: docker run -it --rm wpscanteam/wpscan --url http://[yourbloghere.com] --enumerate t
Does CEF replace a Web Application Firewall (WAF)?
No. CEF and was specifically designed to leave protection against active web attacks to WAFs, which do it best.
Does CEF replace a host firewall?
No. CEF specializes in web-type intelligence and leaves the protection of other services to the host firewall.
Should I keep my WAF and host firewall?
Yes.
Why use CEF then?
CEF helps you earlier in the cyber-attack chain, during the Reconnaissance stage, to disrupt malicious research efforts. Remember, attacks do not necessarily correlate with the research origin(s).
What is an Intent Indicator?
An Intent Indicator is a trait derived from cyber threat intelligence that with high confidence indicates malicious intent. You do not need to activate every Intent Indicator powering CEF if for some reason one or more break your business traffic. E.g. A bank may want to block visitors using Tor to reduce fraud, while an online newspaper may recognize that readers and journalists have an interest in using Tor to avoid censorship and retribution.
How is an Intent Indicator different than an Indicator of Compromise (IoC)?
BLUF: An Intent Indicator is earlier than an IoC. An IOC indicates that a breach already took place, allowing you only to respond after the fact. Intent Indicators are the attacker’s traits, or Tactics, Techniques, and Procedures (TTPs), observable during the recon phase--traits, that with high confidence, would not belong to legitimate visitor traffic and behavior.
更新日志:
- Bug fix: no longer blocking on non-sensitive pages (caching issue)
- Bug fix: async checks now also work for sites not located in the root folder
- CEF now disrupts hacker attempts at plugin and theme gathering/harvesting/enumeration
- CEF now disrupts hacker attempts at username gathering/harvesting/enumeration
- Fakes most current version of PHP
- Permitted HTTP methods safelisting
- Block proxy probes
- Blocked message appears for bad visitors
- General fixes
- Added Wget detection
- Commented out debugging/localhost settings
- Initial public release