Limit Login Attempts Reloaded - Login Security, Brute Force Protection, Firewall
| 开发者 |
wpchefgadget
nikitaglobal |
|---|---|
| 更新时间 | 2025年12月16日 21:17 |
| 捐献地址: | 去捐款 |
| PHP版本: | 3.0 及以上 |
| WordPress版本: | 6.8 |
| 版权: | GPLv2 or later |
标签
下载
详情介绍:
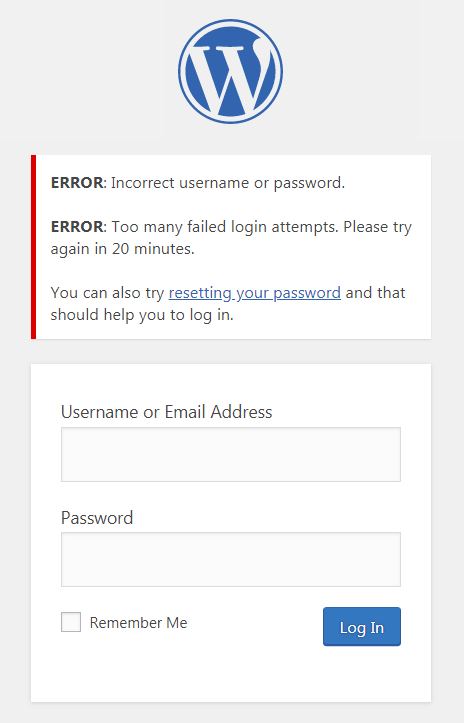
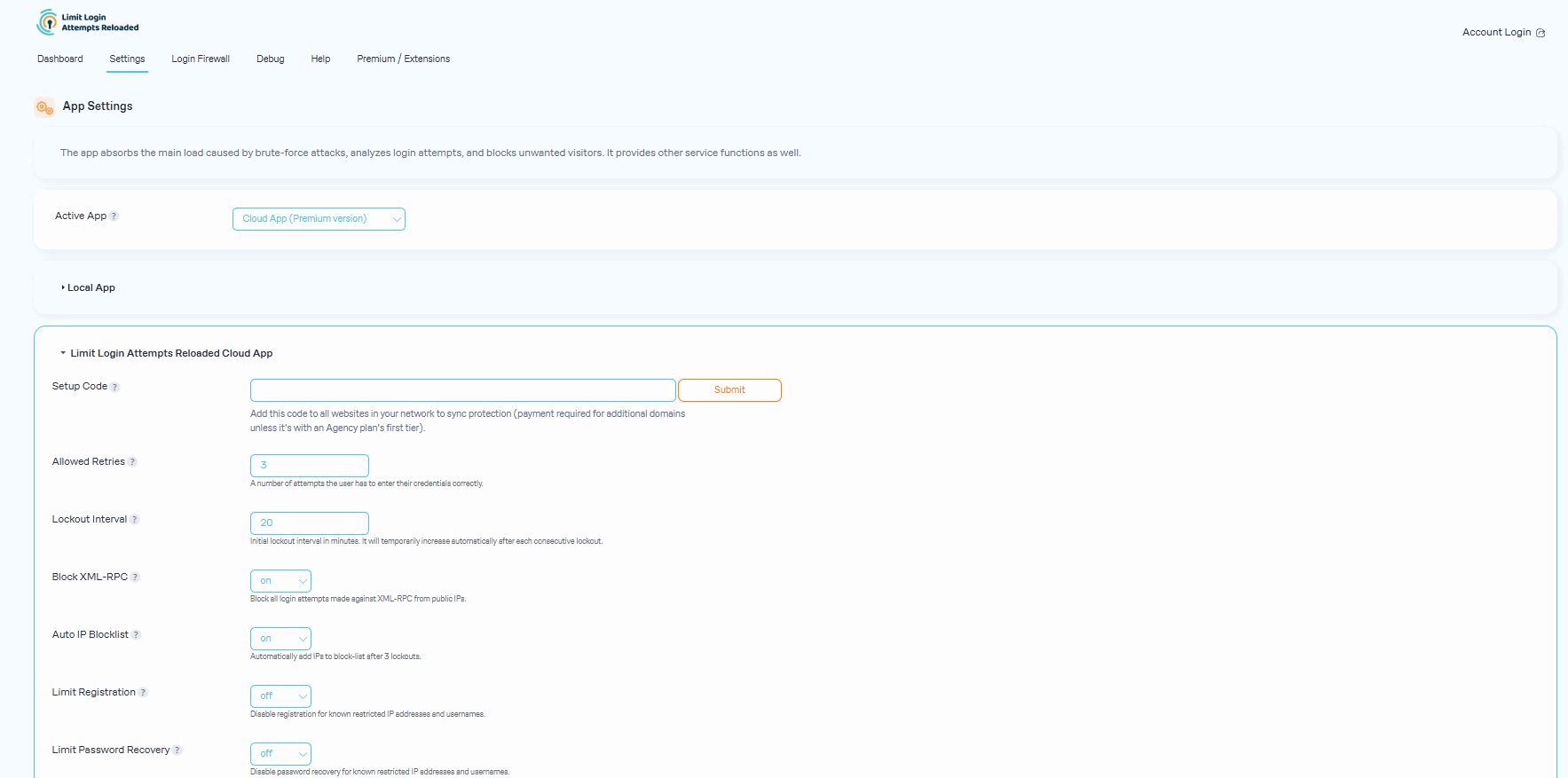
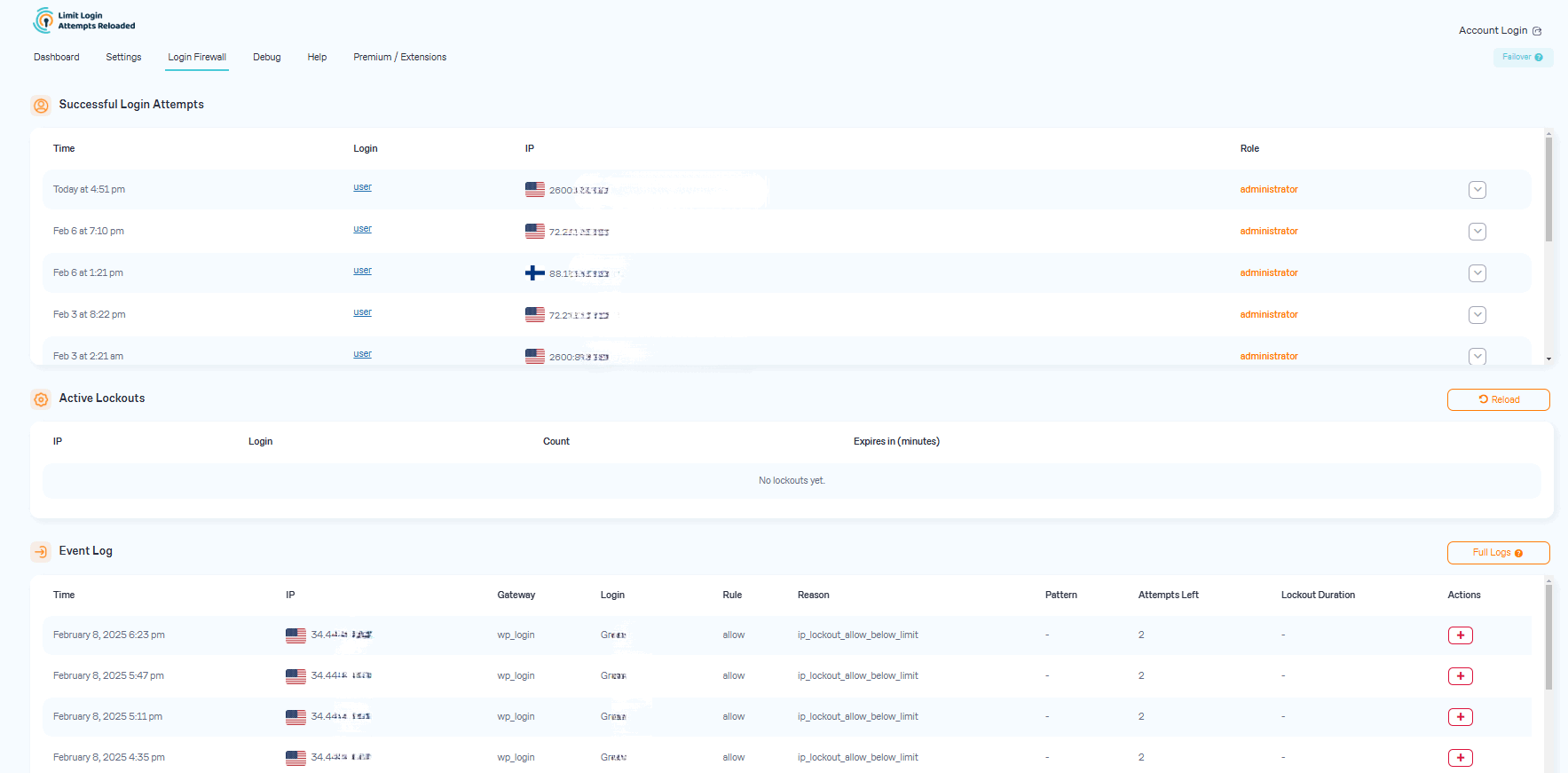
- Limit Logins - Limit the number of retry attempts when logging in (per each IP).
- Configurable Lockout Timings - Modify the amount of time a user or IP must wait after a lockout.
- Remaining Tries - Informs the user about the remaining retries or lockout time on the login page.
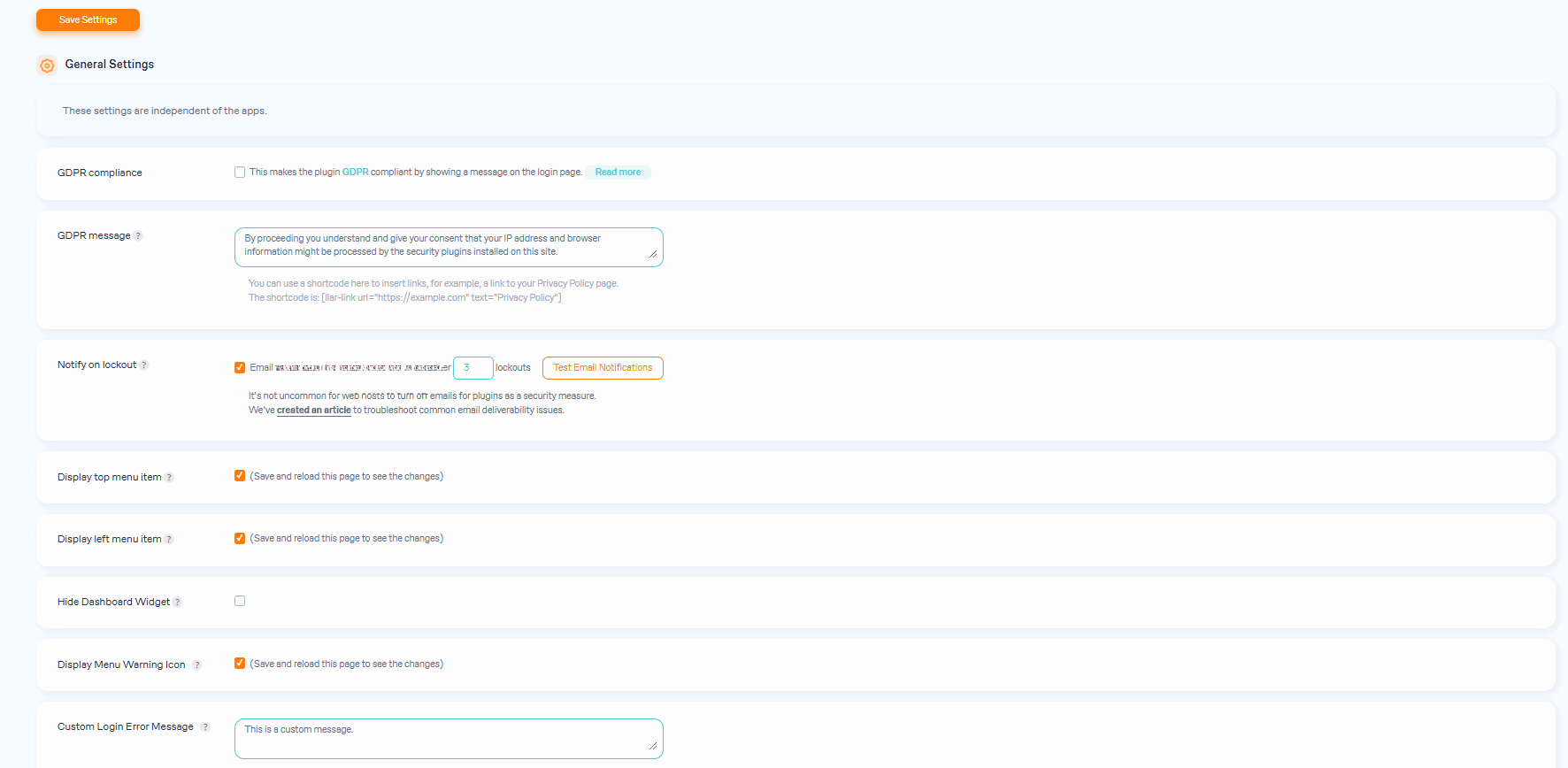
- Lockout Email Notifications - Informs the admin via email of lockouts.
- Denied Attempt Logs - View a log of all denied attempts and lockouts.
- IP & Username Safelist/Denylist - Control access to usernames and IPs.
- New User Registration Protection (Micro Cloud Accounts) - Protects default WP registration.
- Sucuri compatibility.
- Wordfence compatibility.
- Ultimate Member compatibility.
- WPS Hide Login compatibility.
- MemberPress compatibility.
- XMLRPC gateway protection.
- Woocommerce login page protection.
- Multi-site compatibility with extra MU settings.
- GDPR compliant.
- Custom IP origins support (Cloudflare, Sucuri, etc.).
- llar_admin own capability.
- Performance Optimizer - Offload the burden of excessive failed logins from your server to protect your server resources, resulting in improved speed and efficiency of your website.
- Enhanced IP Intelligence - Identify repetitive and suspicious login attempts to detect potential brute force attacks. IPs with known malicious activity are stored and used to help prevent and counter future attacks.
- Enhanced Throttling - Longer lockout intervals each time a malicious IP or username tries to login unsuccessfully.
- Deny By Country - Block logins by country by simply selecting the countries you want to deny.
- Auto IP Denylist - Automatically add IP addresses to your active cloud deny list that repeatedly fail login attempts.
- New User Registration Protection - Protects default WP registration.
- Global Denylist Protection - Utilize our active cloud IP data from thousands of websites in the LLAR network.
- Synchronized Lockouts - Lockout IP data can be shared between multiple domains for enhanced protection in your network.
- Synchronized Safelist/Denylist - Safelist/Denylist IP and username data can be shared between multiple domains.
- Premium Support - Email support with a security tech.
- Auto Backups of All IP Data - Store your active IP data in the cloud.
- Successful Logins Log - Store successful logins in the cloud including IP info, city, state and lat/long.
- Enhanced lockout logs - Gain valuable insights into the origins of IPs that are attempting logins.
- CSV Download of IP Data - Download IP data direclty from the cloud.
- Supports IPV6 Ranges For Safelist/Denylist
- Unlock The Locked Admin - Easily unlock the locked admin through the cloud. *Some features require higher level plans.
- Go to the Plugins section in your site's backend.
- Remove the Limit Login Attempts plugin.
- Install the Limit Login Attempts Reloaded plugin. All your settings will be kept intact!
- Limit Login Attempts Reloaded (correct)
- Limit Login Attempts (incorrect)
屏幕截图:
常见问题:
What do I do if all users get blocked?
If you are using contemporary hosting, it's likely your site uses a proxy domain service like CloudFlare, Sucuri, Nginx, etc. They replace your user's IP address with their own. If the server where your site runs is not configured properly (this happens a lot) all users will get the same IP address. This also applies to bots and hackers. Therefore, locking one user will lead to locking everybody else out. If the plugin is not using our Cloud App, this can be adjusted using the Trusted IP Origin setting. The cloud service intelligently recognizes the non-standard IP origins and handles them correctly, even if your hosting provider does not.
How do I know if I'm under attack?
An easy way to check if the attack is legitimate is to copy the IP address from the lockout notification and check its location using a IP locator tool. If the location is not somewhere you recognize and you have received several failed login attempts, then you are likely being attacked. You might notice dozens or hundreds of IPs each day. Visit our website to learn how can you prevent brute force attacks on your website.
How can I tell that the premium plugin is working?
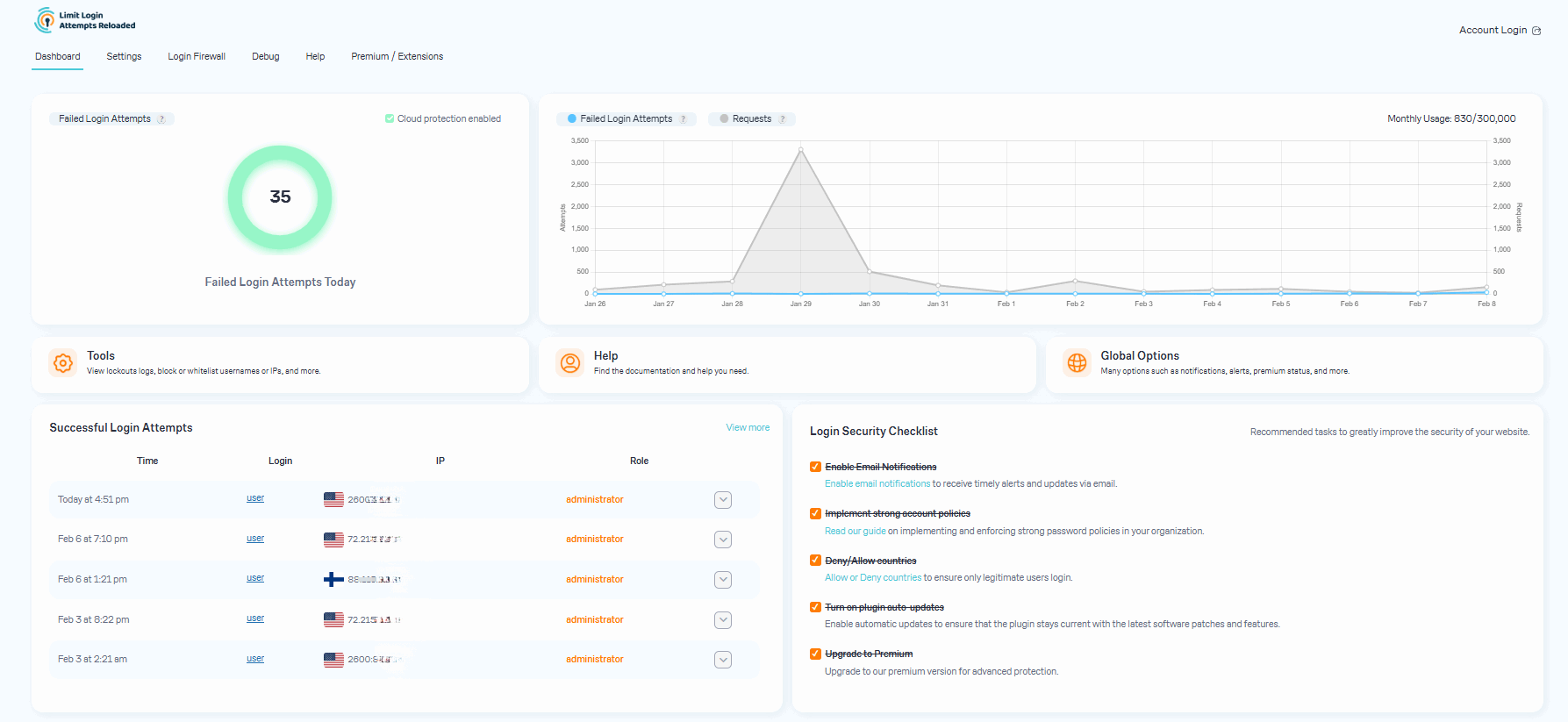
After you upgrade to our premium version, you will see a new dashboard in your WordPress admin that shows all attacks that will now relay through our cloud service. On the graph, you'll see requests and failed login attempts. Each request will represent the cloud app validating an IP, which also includes denied logins. In some cases, you may notice an increase in speed and efficiency with your website. Also, a reduction in lockout notifications via email.
Could these failed login attempts be fake?
Some users find it hard to believe that they could experience numerous unsuccessful login attempts, particularly when their site has just been established or has minimal human traffic. The plugin is not responsible for generating these failed login attempts. Newly created websites are frequently hosted on shared IP addresses, making it easy for hackers to discover them. Additionally, newly registered domain names are often crawled soon after creation, rendering a WordPress website susceptible to attacks. Such websites are attractive targets as security is not a primary concern for their owners. We've created an article that delves deeper into the issue of fake login attempts in WordPress.
What happens if my site exceeds the request limits in the plan?
The premium plan’s resource limits start from 100,000 requests per month, which should accept almost any heavy brute-force attack. We monitor all of our sites and will alert the user if it appears they are going over their limits. If limits are reached, we will suggest to the user upgrading to the next plan. If you are using the free version, the load caused by brute force attacks will be absorbed by your current hosting bandwidth, which could cause your hosting costs to increase.
What do I do if all users get blocked?
If you are using contemporary hosting, it’s likely your site uses a proxy domain service like CloudFlare, Sucuri, Nginx, etc. They replace your user’s IP address with their own. If your server is not configured properly, all users will get the same IP address. This also applies to bots and hackers. Therefore, locking one user will lead to locking everybody else out. In the free version of the plugin, this can be adjusted using the Trusted IP Origin setting. In the premium version, the cloud service intelligently recognizes the non-standard IP origins and handles them correctly, even if your hosting provider does not.
What URLs are being attacked and protected?
The URLs being protected are your login page (wp-login.php, wp-admin), xmlrpc.php, WooCommerce login page, and any custom login page you have that uses regular WordPress login hooks.
Why is LLAR more popular than other brute-force protection plugins?
Our main focus is protecting your site from brute force attacks. This allows our plugin to be very lean and effective. It doesn’t require a lot of your web hosting resources and keeps your site well-protected. More importantly, it does all of this automatically as our service learns on its own about each IP it encounters. In contrast, a firewall would require manual blocking of IPs.
What to do when an admin gets blocked?
Open the site from another IP. You can do this from your cell phone, or using Opera browser and enabling free VPN there. You can also try turning off your router for a few minutes and then see if you get a different IP address. These will work if your hosting server is configured correctly. If that doesn’t work, connect to the site using FTP or your hosting control panel file manager. Navigate to wp-content/plugins/ and rename the limit-login-attempts-reloaded folder. Log in to the site then rename that folder back and whitelist your IP. By upgrading to our premium app, you will have the unlocking functionality right from the cloud so you’ll never have to deal with this issue.
What settings should I use In the plugin?
The settings are explained within the plugin in great detail. If you are unsure, use the default settings as they are the recommended ones.
Can I share the safelist/denylist throughout all of my sites?
By default, you will need to copy and paste the lists to each site manually. For the premium service, sites are grouped within the same private cloud account. Each site within that group can be configured if it shares its lockouts and access lists with other group members. The setting is located in the plugin's interface. The default options are recommended.
更新日志:
- PHP 5.6 compatibility fix.
- Added login URL to notification emails for better debugging.
- Fixed MemberPress compatibility.
- Fixed a popup notice when a user was on the whitelist (local mode).
- Added the individual domain to the notification email subject.
- Updated formatting of the cloud login link.
- Improved onboarding popup behavior.
- Fixed: json_decode(): Passing null to parameter #1 ($json) of type string is deprecated warning.
- Help and extensions page visual changes.
- Assets cleanup.
- Fixed conflict with Hub and similar themes.
- Reorganized links.
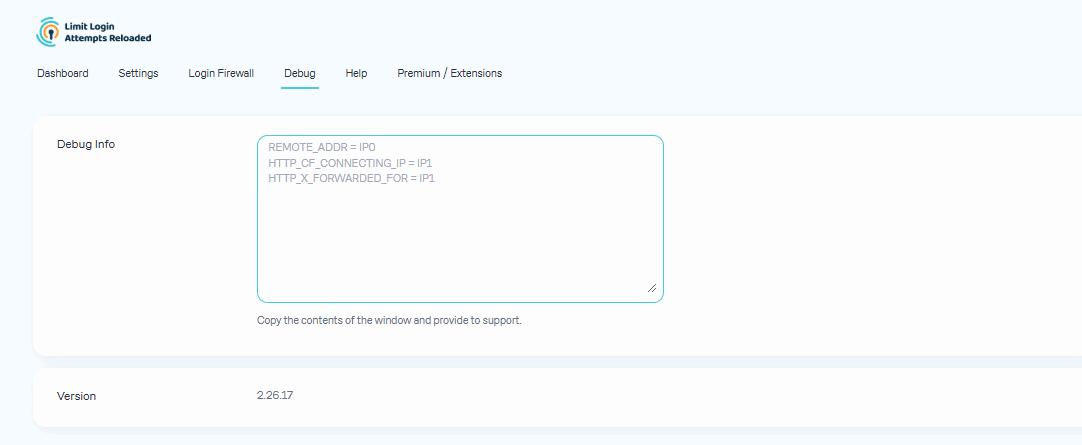
- Fixed REMOTE_ADDR if server is misconfigured.
- Lint.
- Update notice position corrected.
- Debug tab - more info added.
- Lint.
- Fixed formatting issues for Safari on some pages.
- Added displaying of Customer ID.
- Menu minor fix.
- Onboarding process updated.
- Added links to the IP2Location page.
- Better displaying IPv6 in the log.
- Added default registration protection for cloud accounts (free and paid).
- Fixed GDPR message issue for some themes.
- Fixed translation compatibility with WordPress 6.7.
- Fixed GDPR message on the Woocommerce login page.
- Fix: load login-page-styles.css (on wp-login.php) only if it is necessary (thanks to georgejipa).
- CSS fixes.
- Improved compatibility with custom login pages, including WooCommerce and UltimateMember.
- Standardized display of login messages.
- A new Custom Error Message setting is added. The message is being appended to all asynchronous messages.
- Fixed translation compatibility with WordPress 6.7.
- CSS fixes.
- New "llar_admin" capability added to let other roles access the plugin.
- CSS fixes.
- Sticky headers added to the log tables.
- Small interface changes.
- Better displaying IPv6 in successful login attempts block.
- Possible intersections in tabs with other plugins fixed.
- PHP 8, 9 compatibility updates.
- Refactoring.
- Fixed possible style conflicts related to tables.
- Fixed possible PHP warnings.
- Fixed some I18N issues, thanks to alexclassroom!
- Better displaying multiple roles in login logs.
- Log of successful login attempts implemented for Micro Cloud (Free) and Premium users.
- Checklist of recommended actions implemented.
- Settings page reorganized.
- Chart library updated.
- Fixed possible WooCommerce conflict.
- Better informing on Micro Cloud.
- Micro Cloud API url fix.
- Better informing on cloud status.
- Added country translation.
- Better Micro Cloud API response handling.
- A link fixed.
- CSS issue fixed on Logs tab.
- CSS issue fixed.
- Micro Cloud link fixed.
- New design.
- Free Micro Cloud plan introduced.
- A link fixed.
- Improved cloud charts.
- Security improvement: Better shortcode escaping.
- Fixed date formatting on the logs page.
- Fixed top menu links on the front-end.
- Badge added to the top menu.
- Security improvement: Different nonce for each AJAX action.
- Security improvement: The toggle_auto_update_callback checks for the update_plugins cap.
- PHP 8.2/9 compatibility improved, thanks to Jer Turowetz!
- Button size and text typo fixed.
- Better loading of translations.
- Fixed PHP warning related to menu.
- Better side menu.
- Fixed I18N issues, thanks to alexclassroom!
- Interface changes.
- Tested with WP 6.3.
- Optimization: autoload for large options turned off.
- Interface changes.
- Fix against network requests caching removed b/c some misconfigured servers can't handle it.
- Better handling of network connection issues.
- Fixed responsive formatting on dashboard.
- Added fix against network requests caching.
- Fixed errors occurring in situations where two versions of the plugin are installed (which should not normally happen).
- Refactoring.
- Server load reducing optimization.
- Double slashes in paths removed.
- Better handling of cloud response codes.
- Error messages logic fixed.
- Multisite support improved.
- CSS outside of the plugin issue fixed.
- Better number formatting on the dashboard.
- Lockout email template updated.
- Ultimate Member compatibility.
- Fixed conflicting URL parameters in some rare cases.
- Updated attempts counter logic.
- Fixed IPv4 validation when passed with a port number.
- Fixed texts and translations.
- PHP 8 compatibility fixed.
- Logs loading issue fixed.
- Help and Extensions tabs added.
- Notification about auto updates added.
- Displaying of plugin version added.
- Text changes made.
- Tested with PHP 8.
- Small styles refactoring.
- Fixed a rare issue with events log not being displayed correctly.
- Chart library updated.
- Welcome page replaced with a modal.
- Email text, links updated.
- Country flags added to log.
- Refresh button added to log.
- Email text updated.
- Email links updated.
- Fixed Woocommerce integration.
- Updated some interface links.
- Fixed session error in rare cases.
- Access rules explained.
- Improved session behavior on the login page.
- Fixed warning on some GoDaddy installations.
- Improved compatibility with WordFence.
- Better handling of HTTP_X_FORWARDED_FOR on Debug tab.
- Added option to hide warning badge.
- Security indicator fixed for multisite.
- Added setting to turn the dashboard widged off.
- The widget is visible to admins only.
- Dashboard widged added.
- Security indicator added.
- Fixed E_ERROR occurring in rare cases when the log table is corrupted.
- Protection increased: bots can't parse lockout messages anymore.
- Cloud: better unlock UX.
- Litle cleanup.
- Added infinite scroll for cloud logs.
- Reduced plugin size by removing obsolete translations.
- Cleaned up the dashboard.
- Cloud: added information about auto/manually-blocked IPs.
- GDPR: added an option to insert a link to a Privacy Policy page via a shortcode, clarified GDPR compliance.
- IP added to the email subject.
- Added support of CIDR notation for specifying IP ranges.
- Texts updated.
- Refactoring.
- Fixed: Uncaught Error: Call to a member function stats()
- Cloud API: added block by country.
- Refactoring.
- GDPR compliance: IPs obfuscation replaced with a customizable consent message on the login page.
- Cloud API: fixed removing of blocked IPs from the access lists under certain conditions.
- Cloud API: domain for Setup Code is taken from the WordPress settings now.
- Multisite tab links fixed.
- Option to show and hide the top-level menu item.
- Sucuri compatibility verified.
- Wordfence compatibility verified.
- Better menu navigation.
- Timezones fixed for the global chart.
- More clear wording.
- Cloud API: fixed double submit in the settings form.
- Better displaying of stats.
- Updated email text.
- New dashboard more clear stats.
- New dashboard with simple stats.
- Texts and links updated.
- Welcome page.
- Image and text updates.
- Refactoring.
- Feedback message location fixed.
- Text changes.
- Cloud API: usage chart added.
- Text changes.
- Missing jQuery images added.
- PHP 5 compatibility fixed.
- Custom App setup link replaced with setup code.
- Plugin pages message.
- Lockout notification refactored.
- CSS cache issue fixed.
- Notification text updated.
- Refactoring.
- Email text and notification updated.
- New links in the list of plugins.
- Custom Apps functionality implemented. More details: https://limitloginattempts.com/app/
- Alternative method of closing the feedback message.
- Refactoring.
- Reset password feature has been removed as unwanted.
- Small refactoring.
- BuddyPress login error compatibility implemented.
- UltimateMember compatibility implemented.
- A PHP warning fixed.
- Fixed incompatibility with PHP < 5.6.
- Settings page layout refactored.
- The feedback message is shown for admins only now, and it can also be closed even if the site has issues with AJAX.
- Fixed the feedback message not being shown, again.
- Fixed the feedback message not being shown.
- Small refactoring.
- get_message() - fixed error notices.
- This is the first time we are asking you for a feedback.
- Blacklisted usernames can't be registered anymore.
- Fixed: GDPR compliance option could not be selected on the multisite installations.
- Debug information has been added for better support.
- 已添加“可信 IP 起源”选项。
- Extra lockout options are back.
- The plugin doesn't trust any IP addresses other than _SERVER["REMOTE_ADDR"] anymore. Trusting other IP origins make protection useless b/c they can be easily faked. This new version provides a way of secure IP unlocking for those sites that use a reverse proxy coupled with misconfigurated servers that populate _SERVER["REMOTE_ADDR"] with wrong IPs which leads to mass blocking of users.
- The lockout alerts can be sent to a configurable email address now.
- Settings page is moved back to "Settings".
- Settings are moved to a separate page.
- Fixed: login error message. https://wordpress.org/support/topic/how-to-change-login-error-message/
- A security issue inherited from the ancestor plugin Limit Login Attempts has been fixed.
- GDPR compliance implemented.
- Fixed: ip_in_range() loop $ip overrides itself causing invalid results. https://wordpress.org/support/topic/ip_in_range-loop-ip-overrides-itself-causing-invalid-results/
- Fixed: the plugin was locking out the same IP address multiple times, each with a different port. https://wordpress.org/support/topic/same-ip-different-port/
- Added support of Sucuri Website Firewall.
- Fixed the issue with backslashes in usernames.
- Plugin returns the 403 Forbidden header after the limit of login attempts via XMLRPC is reached.
- Added support of IP ranges in white/black lists.
- Lockouts now can be released selectively.
- Fixed the issue with encoding of special symbols in email notifications.
- Added Multi-site Compatibility and additional MU settings. https://wordpress.org/support/topic/multisite-compatibility-47/
- 现在可以将用户名和 IP 地址列入白名单和黑名单。 https://wordpress.org/support/topic/banning-specific-usernames/ https://wordpress.org/support/topic/good-831/
- The lockouts log has been inversed. https://wordpress.org/support/topic/inverse-log/
- IP addresses can be white-listed now. https://wordpress.org/support/topic/legal-user/
- A "Gateway" column is added to the lockouts log. It shows what endpoint an attacker was blocked from. https://wordpress.org/support/topic/xmlrpc-7/
- The "Undefined index: client_type" error is fixed. https://wordpress.org/support/topic/php-notice-when-updating-settings-page/
- Removed the "Handle cookie login" setting as they are now obsolete.
- Added bruteforce protection against Woocommerce login page attacks. https://wordpress.org/support/topic/how-to-integrate-with-woocommerce-2/
- Added bruteforce protection against XMLRPC attacks. https://wordpress.org/support/topic/xmlrpc-7/
- The site connection settings are now applied automatically and therefore have been removed from the admin interface.
- Now compatible with PHP 5.2 to support some older WP installations.
- fixed PHP Warning: Illegal offset type in isset or empty https://wordpress.org/support/topic/limit-login-attempts-generating-php-errors
- fixed the deprecated functions issue https://wordpress.org/support/topic/using-deprecated-function
- Fixed error with function arguments: https://wordpress.org/support/topic/warning-missing-argument-2-5
- added time stamp to unsuccessful tries on the plugin configuration page.
- 修复了.po 翻译文件问题。
- code refactoring and optimization.