Plugin Inspector
| 开发者 | gioni |
|---|---|
| 更新时间 | 2019年2月15日 23:57 |
| 捐献地址: | 去捐款 |
| PHP版本: | 3.3 及以上 |
| WordPress版本: | 5.1 |
| 版权: | GPLv2 |
详情介绍:
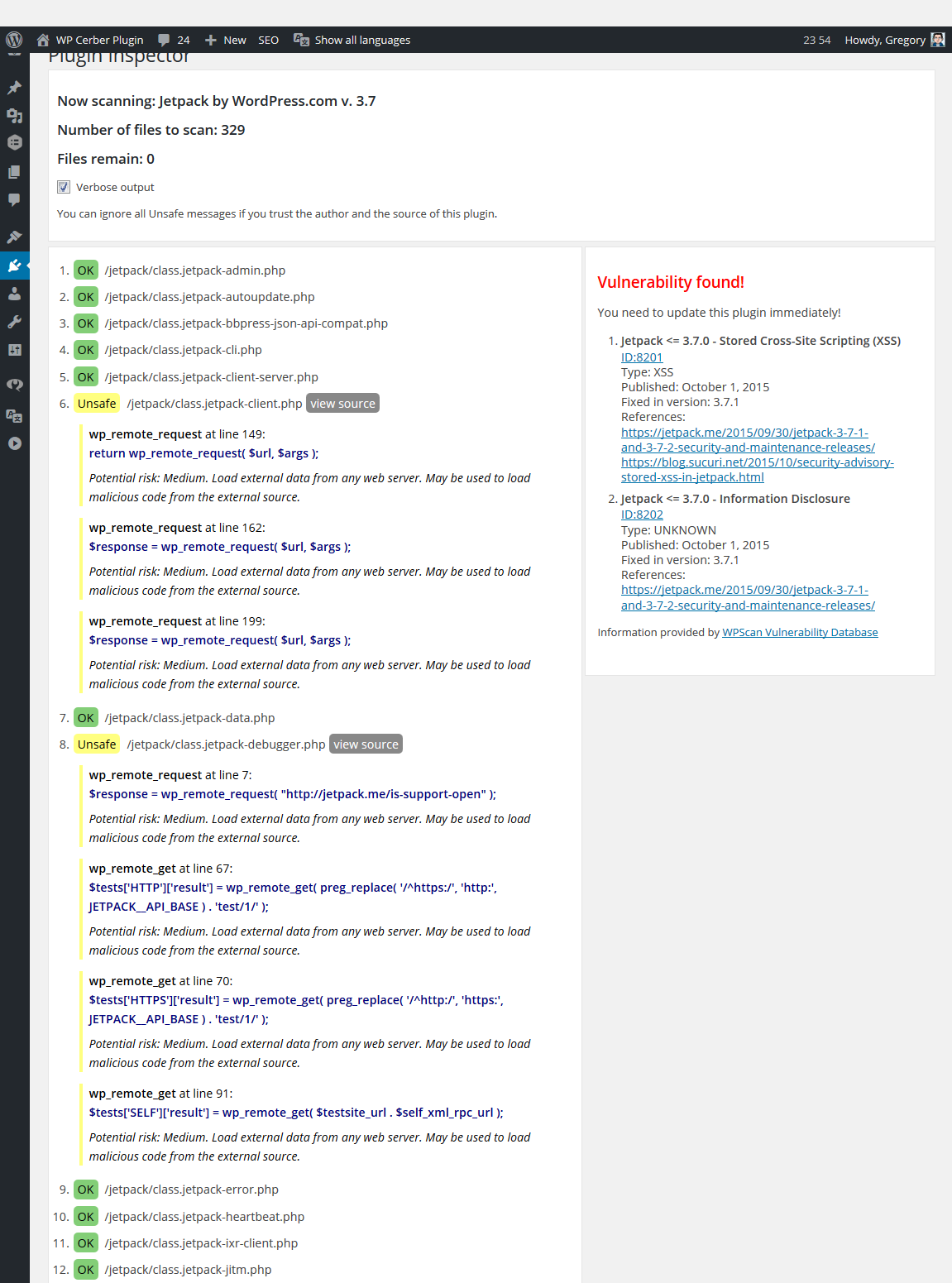
The Plugin Inspector plugin is an easy way to check plugins installed on your WordPress and make sure that plugins do not use deprecated WordPress functions and some unsafe functions like eval, base64_decode, system, exec, etc. Some of those functions may be used to load malicious code (malware) from the external source directly to the site or WordPress database.
Features
- Scans plugins for deprecated WordPress functions
- Scans plugins for unsafe functions like eval, base64_decode, system, exec, etc.
- Checks plugins to find vulnerabilities listed in WPScan Vulnerability Database
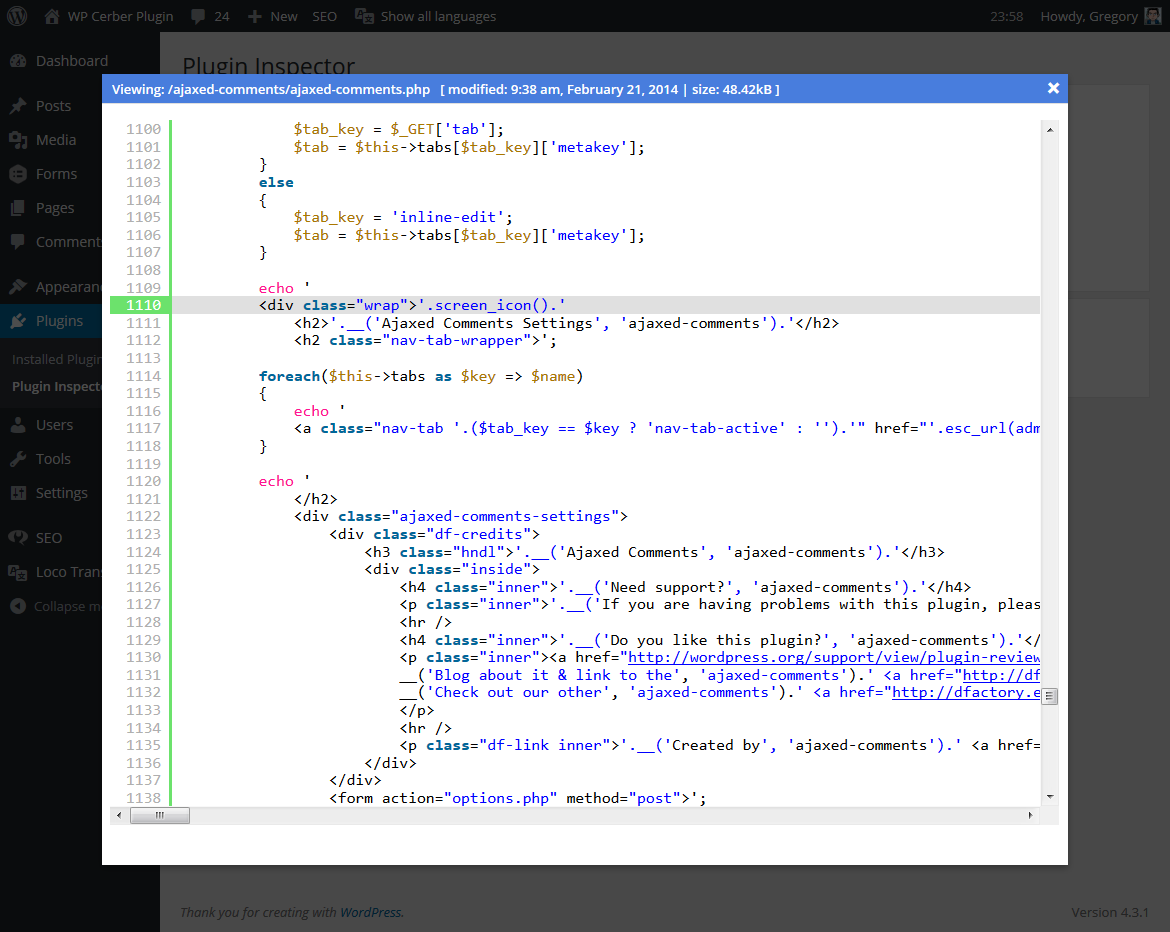
- Beautiful source code viewer with highlighting
安装:
- Upload the Plugin Inspector folder to the plugins directory in your WordPress installation.
- Activate the plugin through the WordPress admin interface.
屏幕截图:
常见问题:
What PHP functions Plugin Inspector treats as unsafe?
Generally, most of those functions are safe, but under certain circumstances those functions may be used to hack site or to load and execute malicious code (malware). This list is not full and will be constantly updating. Any suggestions are welcome.
- eval
- system
- base64_decode
- shell_exec
- exec
- assert
- passthru
- pcntl_exec
- proc_open
- popen
- dl
- create_function
- call_user_func
- call_user_func_array
- file_get_contents
- socket_create
- curl_exec
- wp_remote_request
- wp_remote_get
- wp_remote_post
- wp_safe_remote_post
- wp_remote_head
更新日志:
1.5
- Added cool and convenient code viewer to view found issues in the PHP code.
- Code optimization
- Initial version