Vigilante - 100% Free Security Suite: Firewall, 2FA, Login, Headers, Scanner…
| 开发者 |
fernandot
ayudawp |
|---|---|
| 更新时间 | 2026年2月17日 20:04 |
| PHP版本: | 7.4 及以上 |
| WordPress版本: | 6.9 |
| 版权: | GPL v2 or later |
| 版权网址: | 版权信息 |
详情介绍:
- Firewall rules against common attacks (SQL injection, XSS, file inclusion)
- Security headers for browser protection
- Login attempt monitoring
- XML-RPC blocking
- WordPress version hiding
- Sensitive file protection (.htaccess, wp-config.php)
- Automatic backup of your existing configuration files
- JavaScript challenge - Every visitor must pass an automatic browser verification before accessing your site. Real browsers solve it in seconds, bots get blocked completely
- Aggressive rate limiting - Requests limited to 30 per minute with 15-minute blocks for offenders
- HTTP method restriction - Only GET, POST, and HEAD allowed. PUT, DELETE, PATCH, OPTIONS, and TRACE are blocked
- Empty user agent blocking - Requests without a user agent header are rejected
- Full XML-RPC lockdown - All XML-RPC access is blocked during the attack
- REST API restriction - Only authenticated users can access the REST API
- Auto-deactivation - Mode automatically turns off after 4 hours so you never forget it's on
- Email notifications - Get notified when the mode is activated and deactivated
- HMAC-signed cookies - Verified visitors receive a cryptographically signed cookie so they only see the challenge once
- One-time verification codes sent via email
- Trusted devices feature - skip 2FA on recognized devices for 30 days
- Role-based enforcement - require 2FA for administrators, editors, or any role
- Easy code resend functionality
- Configurable code expiry and attempt limits
- SQL injection blocking
- XSS (Cross-Site Scripting) attack prevention
- File inclusion protection (LFI/RFI)
- Directory traversal blocking
- Bad bot detection and blocking
- Rate limiting against DDoS and brute force
- IP whitelist and blacklist management
- HTTP method restriction
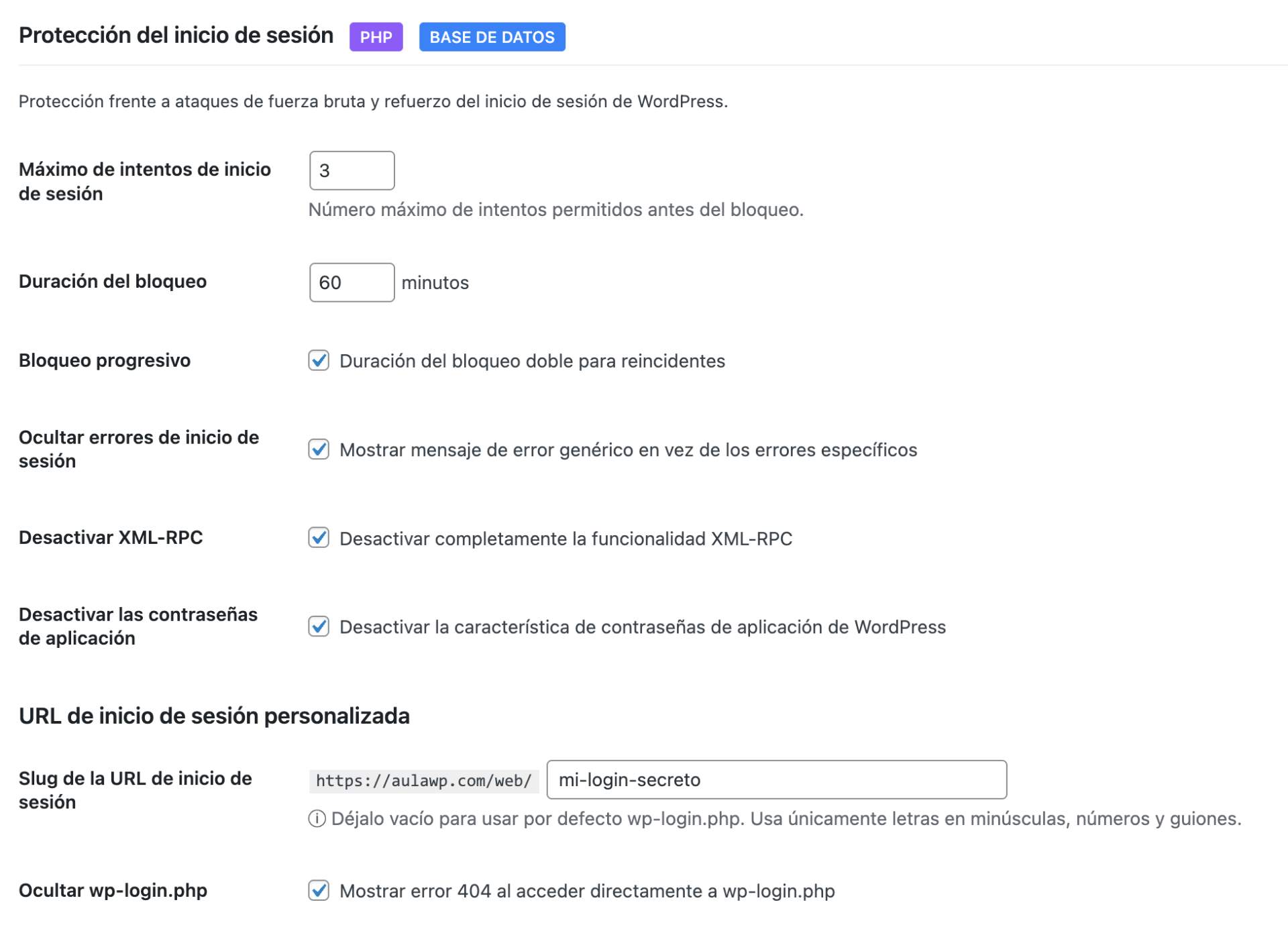
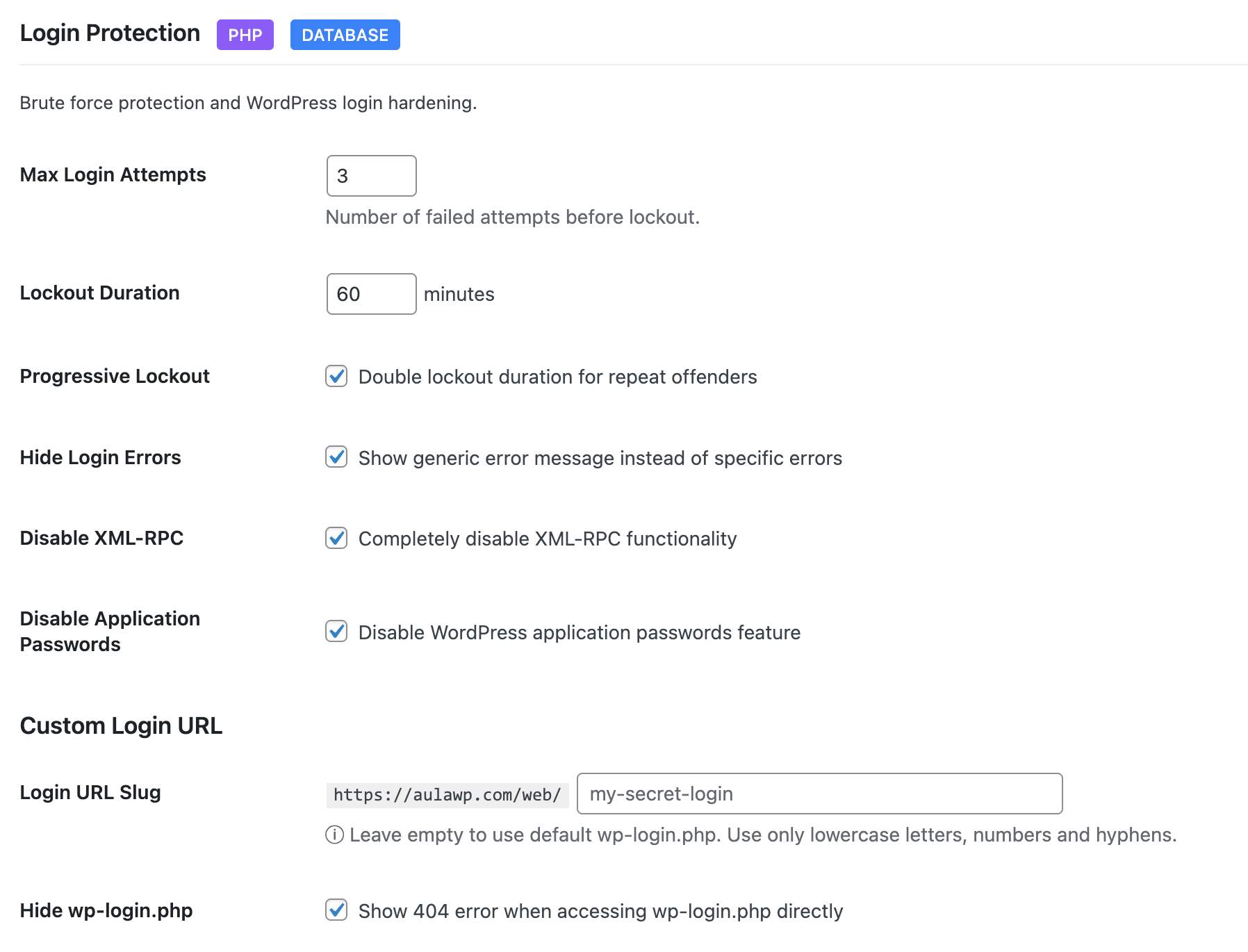
- Limit login attempts with configurable thresholds
- Progressive lockouts - longer blocks for repeat offenders
- Custom login URL - hide wp-login.php from bots
- Hide login error messages - don't reveal valid usernames
- XML-RPC disable - block this common attack vector
- Application passwords control
- Admin login notifications via email
- IP whitelist for trusted locations
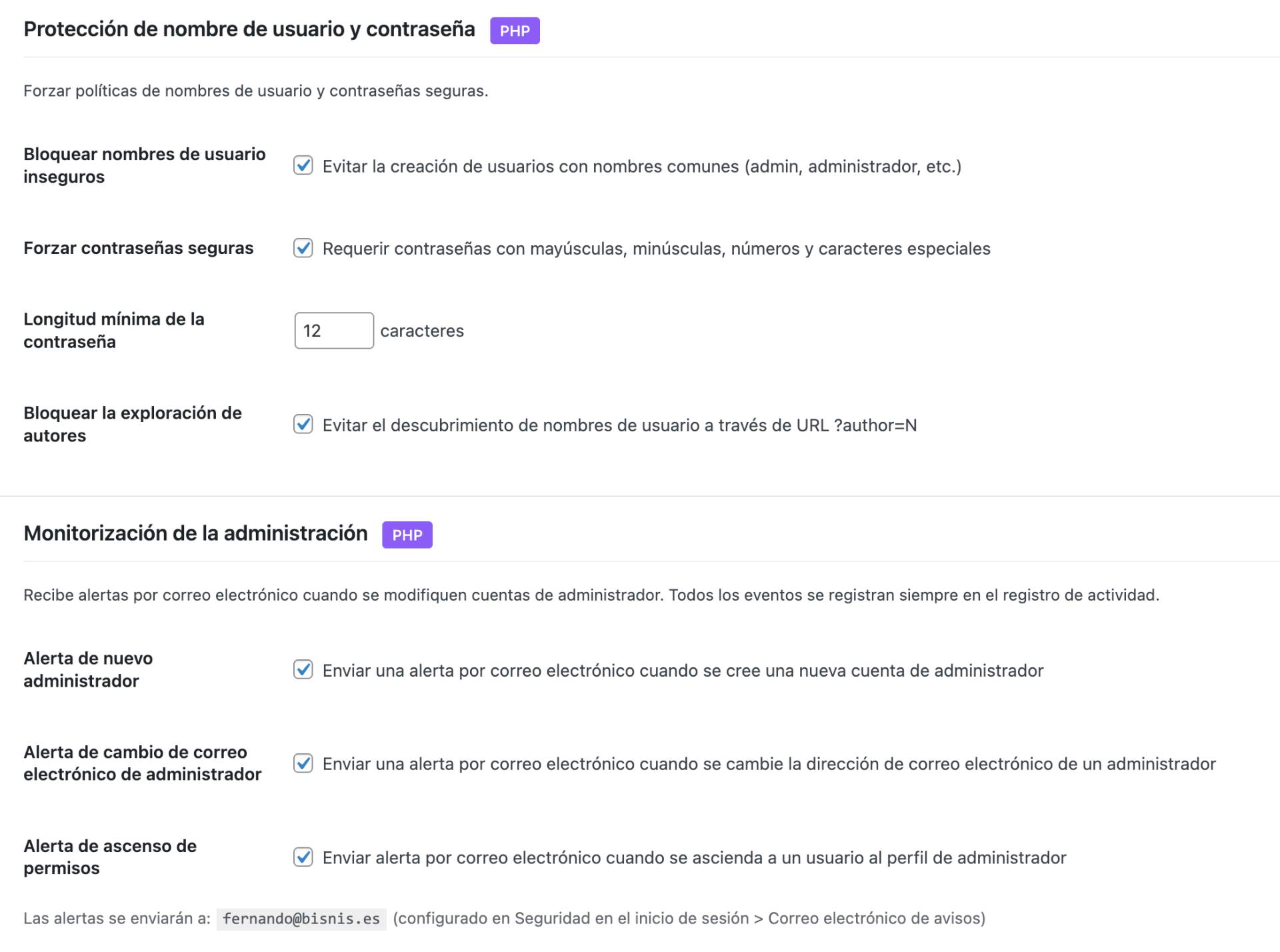
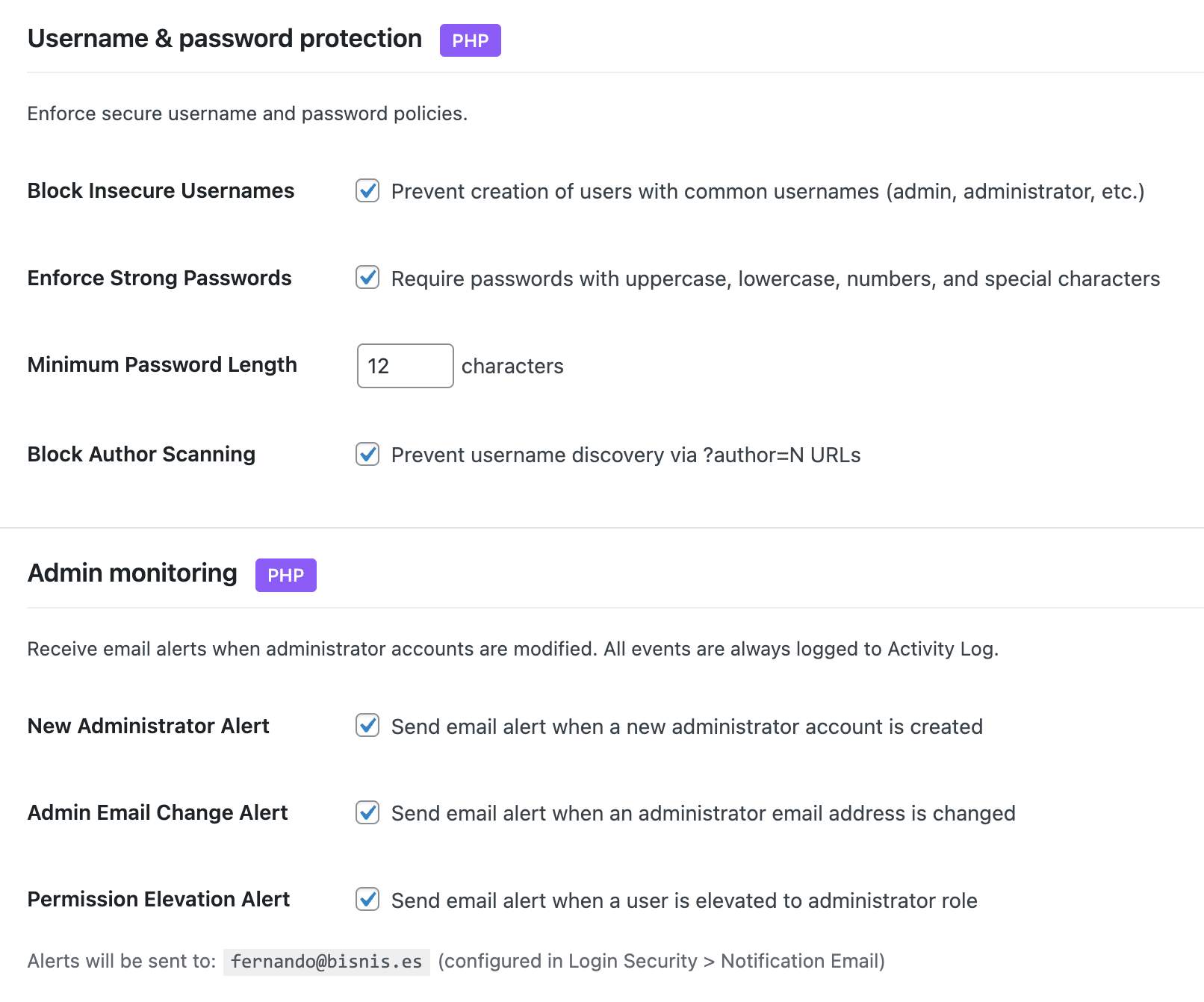
- Block insecure usernames (admin, test, root, etc.)
- Force strong passwords with minimum length
- Password expiration with configurable intervals
- Password history - prevent reusing old passwords
- Force password reset for all users (post-hack recovery)
- Session limits - control concurrent logins per user
- Session management - view and revoke active sessions
- Email verification for new registrations
- Registration approval workflow - manually approve new users
- Admin account monitoring - alerts for new admins, email changes, privilege escalation
- Content Security Policy (CSP) with visual builder
- HSTS (HTTP Strict Transport Security) with preload option
- X-Frame-Options - prevent clickjacking
- X-Content-Type-Options - prevent MIME sniffing
- Referrer Policy control
- Permissions Policy (camera, microphone, geolocation)
- Cross-Origin policies (COEP, COOP, CORP)
- HTTPS enforcer with automatic mixed content fix
- Built-in header testing tool
- WordPress core verification against official checksums
- Plugin file monitoring
- Theme file checking
- Uploads directory scanning for PHP files
- Suspicious code pattern detection (eval, base64_decode, shell_exec)
- Scheduled automatic scans (hourly, daily, weekly)
- Email alerts when changes are detected
- Excluded paths configuration
- Successful and failed login attempts
- Two-factor authentication events
- User account changes (creation, deletion, role changes)
- Content modifications (posts, pages)
- Plugin and theme activations/deactivations
- Security events and blocked threats
- Configurable retention period
- Export logs to CSV
- Filter by event type, user, or date
- wp-config.php security constants (DISALLOW_FILE_EDIT, etc.)
- Comment spam protection with honeypot fields
- Disable pingbacks and trackbacks
- Close comments on old posts
- WordPress head cleanup (remove version, RSD, WLW links)
- Feed management and security
- Three access modes: public, authenticated only, or selective
- Block user enumeration via REST API
- Protect sensitive endpoints
- Maintain compatibility with popular plugins (WooCommerce, Contact Form 7, Elementor)
- Export/Import Settings - Transfer your configuration between sites
- Manual Backup - Create backups of .htaccess and wp-config.php on demand
- Reset to Defaults - Start fresh with one click
安装:
- Upload the plugin files to
/wp-content/plugins/vigilante/or install directly from the WordPress plugin repository - Activate the plugin through the 'Plugins' menu in WordPress
- Go to 'Vigilante' in the admin menu
- Apply a security preset or customize individual module settings
- WordPress 6.2 or higher
- PHP 7.4 or higher
- Apache or LiteSpeed server (for .htaccess features)
- SSL certificate recommended for HSTS
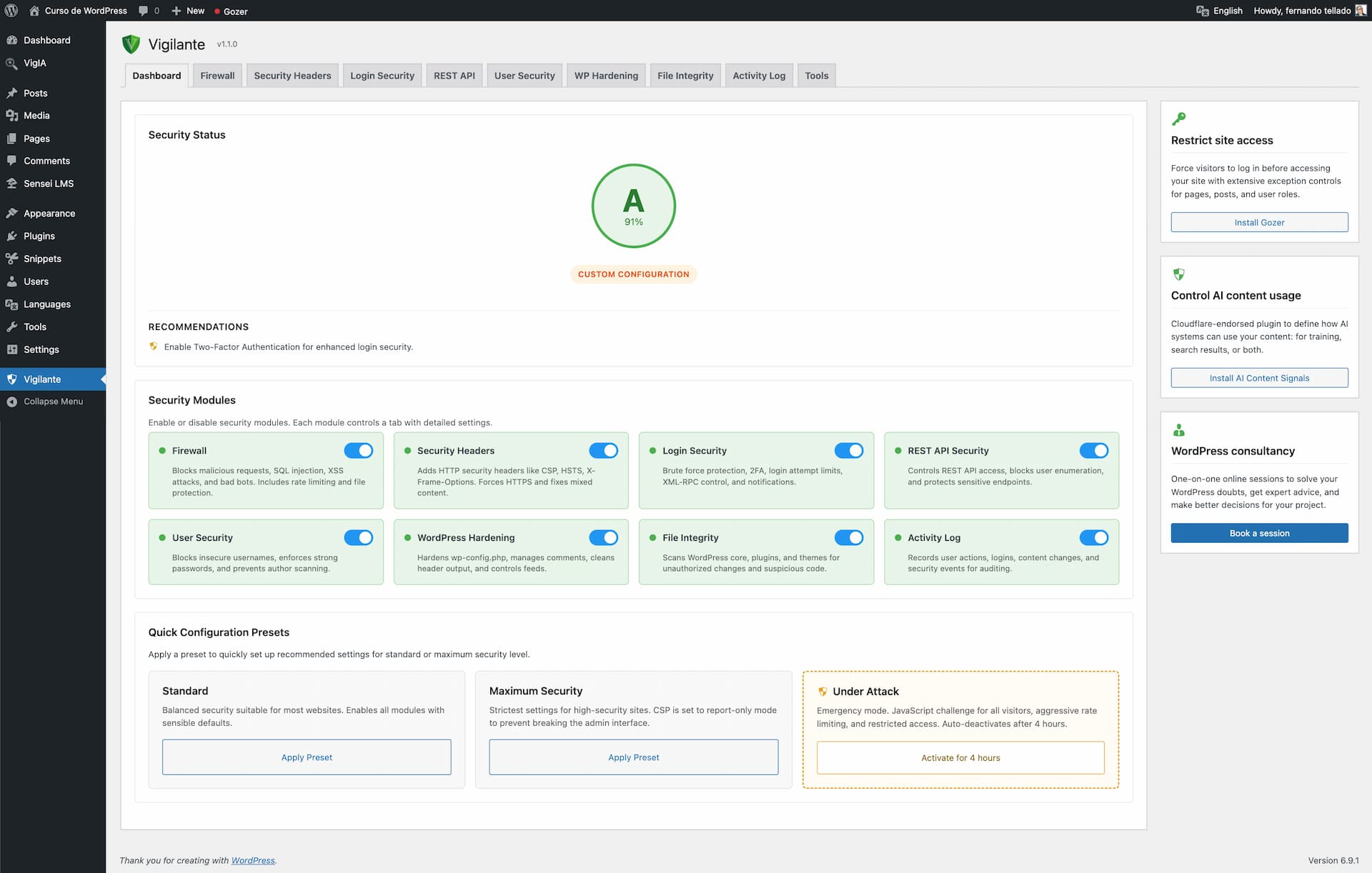
屏幕截图:
常见问题:
Will this plugin slow down my site?
No. Vigilante is optimized for performance. The firewall uses efficient pattern matching, database queries are cached with transients, and .htaccess rules execute at server level before PHP even loads.
What happens when I activate the plugin?
Vigilante immediately creates a backup of your existing .htaccess and wp-config.php files, then applies default security settings. All modules are enabled with balanced defaults suitable for most sites.
What happens when I deactivate the plugin?
All security modifications are automatically reverted. The .htaccess rules are removed, wp-config.php constants are restored to their original values, and scheduled tasks are cleared. Your site returns to its pre-Vigilante state.
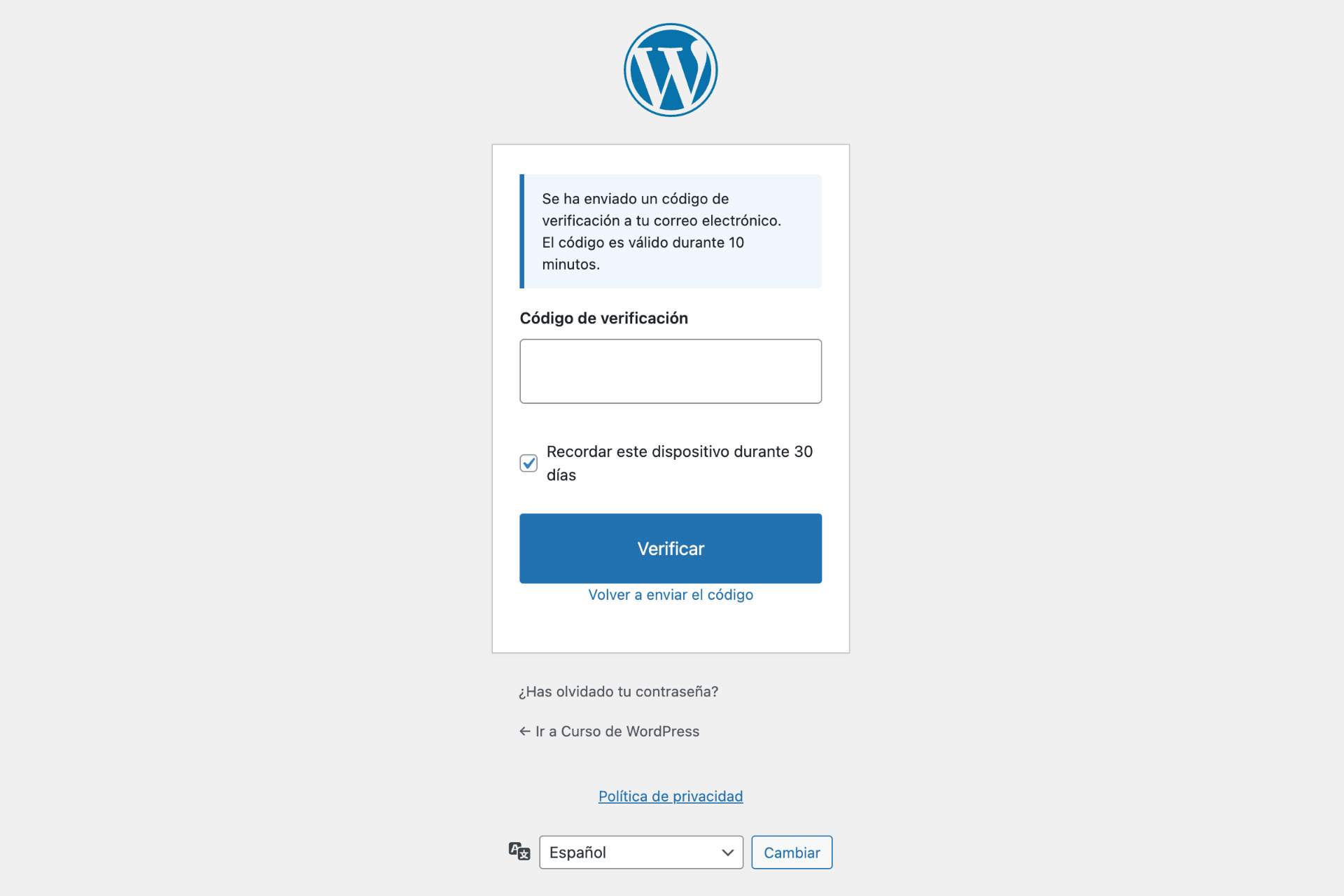
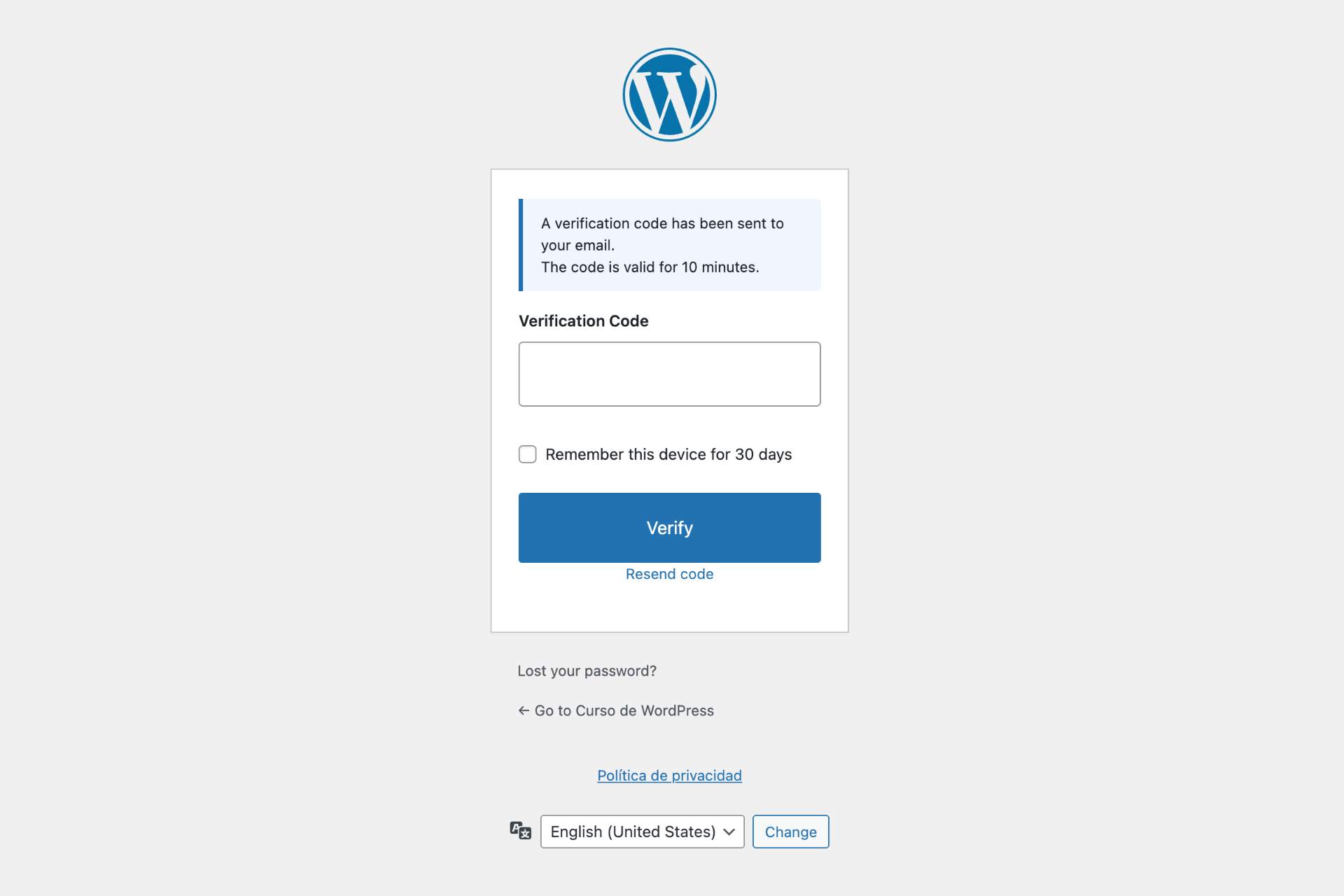
How does two-factor authentication work?
After entering your username and password, you receive a 6-digit verification code via email. Enter this code to complete login. You can optionally mark your device as trusted to skip 2FA for 30 days on that browser.
What if I don't receive the 2FA code?
Check your spam folder first. You can click "Resend code" on the verification form. Codes expire after 10 minutes by default. If issues persist, an administrator can temporarily disable 2FA from the plugin settings.
Which user roles require 2FA?
By default, 2FA is enforced for administrators and editors. You can customize which roles require 2FA in the Login Security settings, or exclude specific users.
How do I recover if I'm locked out?
Access your site via FTP/SFTP and either rename the plugin folder to disable it temporarily, or delete the vigilante_login_attempts table rows for your IP address in the database.
Will the firewall block legitimate users?
The firewall is configured to allow normal WordPress operations, including the block editor, REST API, and popular page builders. If you experience issues, you can whitelist specific IPs or adjust rate limiting thresholds.
Can I use this with other security plugins?
While Vigilante works standalone, running multiple security plugins can cause conflicts. We recommend testing in a staging environment first if you need to combine security solutions.
Does this work with caching plugins?
Yes. Vigilante is compatible with popular caching plugins. The firewall runs before cache layers, and .htaccess rules don't interfere with caching mechanisms.
Does this work with WooCommerce?
Yes. Vigilante includes compatibility settings for WooCommerce. The REST API security module automatically allows WooCommerce endpoints, and the firewall won't block payment gateway connections.
How do I test my security headers?
Use the built-in header testing tool in the Security Headers tab, or visit securityheaders.com with your site URL to get a security grade.
What is password expiration?
You can require users to change their passwords after a set number of days (30, 60, 90, etc.). Users receive warnings before expiration and are forced to change their password on next login when it expires. Password history prevents reusing recent passwords.
What is registration approval?
When enabled, new user registrations require manual approval by an administrator before the account becomes active. Pending users cannot log in until approved. You can configure auto-rejection after a set number of days.
What does email verification do?
New users must verify their email address by clicking a link before their account becomes active. This prevents fake registrations and ensures valid contact information.
How do session limits work?
You can limit how many concurrent sessions each user can have. When the limit is reached, either the new login is blocked or the oldest session is terminated, depending on your configuration.
Can I export the activity log?
Yes. The activity log can be exported to CSV format for external analysis or compliance reporting. You can also filter logs by event type, user, or date range before exporting.
What files does the integrity scanner check?
The scanner compares WordPress core files, plugin files, and theme files against official checksums from WordPress.org. It also scans the uploads directory for suspicious PHP files and detects common malware patterns.
How often does the file integrity scan run?
You can configure automatic scans to run hourly, daily, or weekly. You can also run manual scans at any time. When changes are detected, you can receive email notifications.
What is the difference between Standard and Maximum presets?
Standard applies balanced settings suitable for most sites. Maximum applies stricter rules: lower rate limits, tighter CSP policies, required admin notifications, session limits, and more aggressive hardening. Maximum may require adjustments for sites with complex functionality.
Where are backups stored?
Backups are stored in wp-content/vigilante-backups/. This location persists through plugin updates. The directory is protected with .htaccess rules to prevent direct access.
What is Under Attack mode?
Under Attack mode is an emergency feature you can activate when your site is experiencing an active attack. It adds a JavaScript challenge that real browsers solve automatically in a few seconds, while bots and automated scripts are blocked completely. It also applies aggressive rate limiting, blocks restricted HTTP methods, and restricts API access.
Will Under Attack mode affect my logged-in users?
No. Logged-in users, admin pages, cron jobs, AJAX requests, and the login page are all excluded from the JavaScript challenge. Only unauthenticated frontend visitors see the verification page.
What if I forget to turn off Under Attack mode?
It automatically deactivates after 4 hours. You will also receive an email notification when it activates and deactivates.
Does Under Attack mode change my regular security settings?
No. It operates independently from your preset configuration (Standard or Maximum). Your regular settings are untouched and continue working normally after Under Attack mode deactivates.
更新日志:
- New: Under Attack mode - Emergency JavaScript challenge protection with one-click activation
- New: Automatic browser verification with proof-of-work challenge for frontend visitors
- New: HMAC-signed verification cookies to prevent cookie forgery
- New: Aggressive rate limiting (30 req/min) and HTTP method restriction during attacks
- New: Auto-deactivation after 4 hours with email notifications
- New: REST API and XML-RPC lockdown during Under Attack mode
- New: Non-dismissible admin notice with link to dashboard while mode is active
- Fixed: File Integrity scan results are now fully translatable
- Fixed: File Integrity scanner now reliably detects suspicious files in uploads
- Improved: Uploads directory is now scanned first for faster malware detection
- Improved: Scan time limit increased from 25 to 60 seconds for thorough scanning
- Improved: File limit in uploads scan increased from 2,000 to 10,000 files
- Fixed: Security Headers test button and results are now fully translatable
- Improved: Custom plugin icon now displayed in settings page header
- Improved: Activation notice now includes shield dashicon
- Improved: Settings page now uses full available width for better tab display
- Fixed: REST API compatibility with plugins using PUT/DELETE methods
- Fixed: wp-config.php constant insertion now works correctly on non-English WordPress installations
- Fixed: WP Hardening options now properly apply when unchecking (disabling) settings
- Fixed: Custom configuration detection now triggers when changing any section settings
- Fixed: Corrupted UTF-8 characters in activity log messages and CSS
- Improved: Custom login URL now automatically enables wp-login.php redirect to 404
- Improved: Session limits no longer exclude administrators by default for better security
- Improved: Dashboard "Custom Configuration" badge now uses more visible orange color
- Improved: htaccess HTTP method restrictions now exclude REST API endpoints
- Initial release
- Two-factor authentication via email with trusted device support
- Role-based 2FA enforcement
- Advanced PHP-based firewall with SQL injection, XSS, and file inclusion protection
- Rate limiting with configurable thresholds
- IP whitelist and blacklist management
- Complete security headers implementation (CSP, HSTS, X-Frame-Options, Permissions Policy)
- Built-in security header testing tool
- HTTPS enforcer with mixed content detection
- Login security with brute force protection and progressive lockouts
- Custom login URL support
- XML-RPC and application passwords control
- User security with insecure username blocking
- Strong password enforcement with minimum length
- Password expiration with history tracking
- Force password reset for all users
- Session management and concurrent session limits
- Email verification for new registrations
- Registration approval workflow
- Admin account monitoring and alerts
- WordPress hardening (wp-config constants, comment security, head cleanup)
- Feed management and security
- REST API security with selective endpoint protection
- User enumeration prevention
- Activity log with configurable event tracking
- Log export to CSV and filtering
- File integrity monitoring against WordPress.org checksums
- Scheduled scans with email notifications
- Suspicious code pattern detection
- Settings export and import
- Manual backup creation tool
- Two configuration presets (Standard, Maximum Security)
- Automatic backup and restoration system
- Clean rollback on deactivation
- Full admin interface with tabbed settings