Website Security Check
| 开发者 | johndarrel |
|---|---|
| 更新时间 | 2020年8月27日 15:57 |
| 捐献地址: | 去捐款 |
| PHP版本: | 5.6 及以上 |
| WordPress版本: | 5.5 |
| 版权: | GPLv2 or later |
| 版权网址: | 版权信息 |
详情介绍:
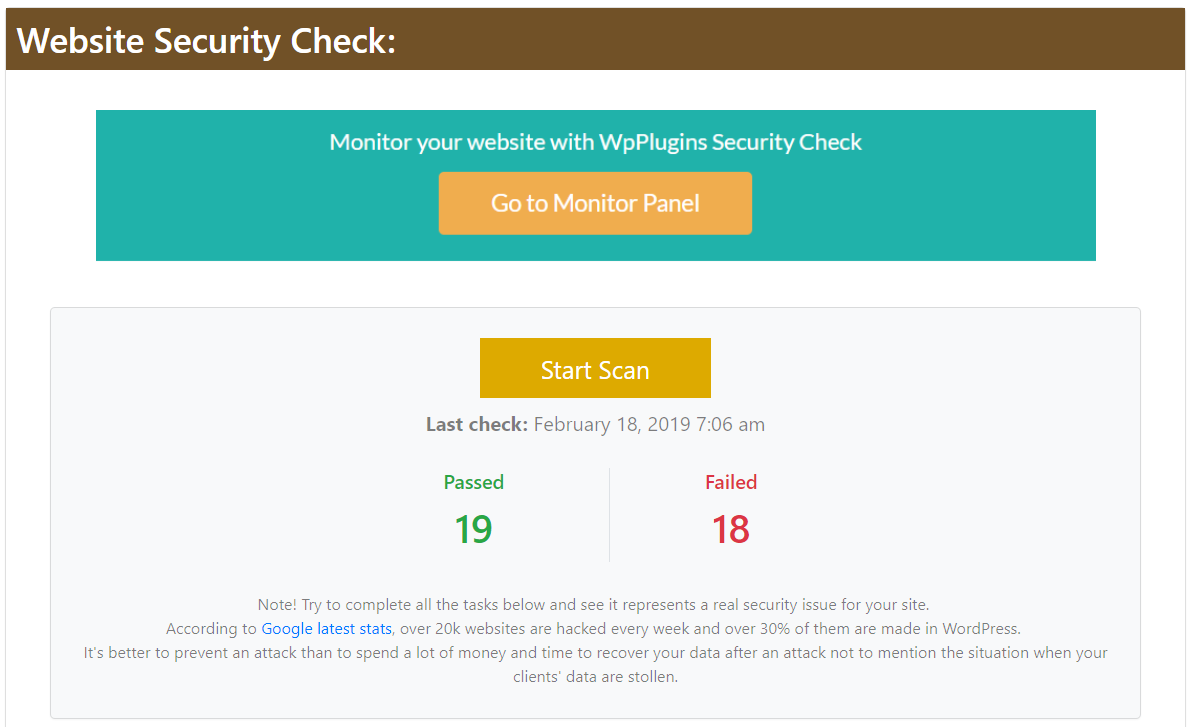
Website Security Check detects if your WordPress website has vulnerabilities and security flaws. Get a full security report for your website.
Check your website with our Free Website Security Check
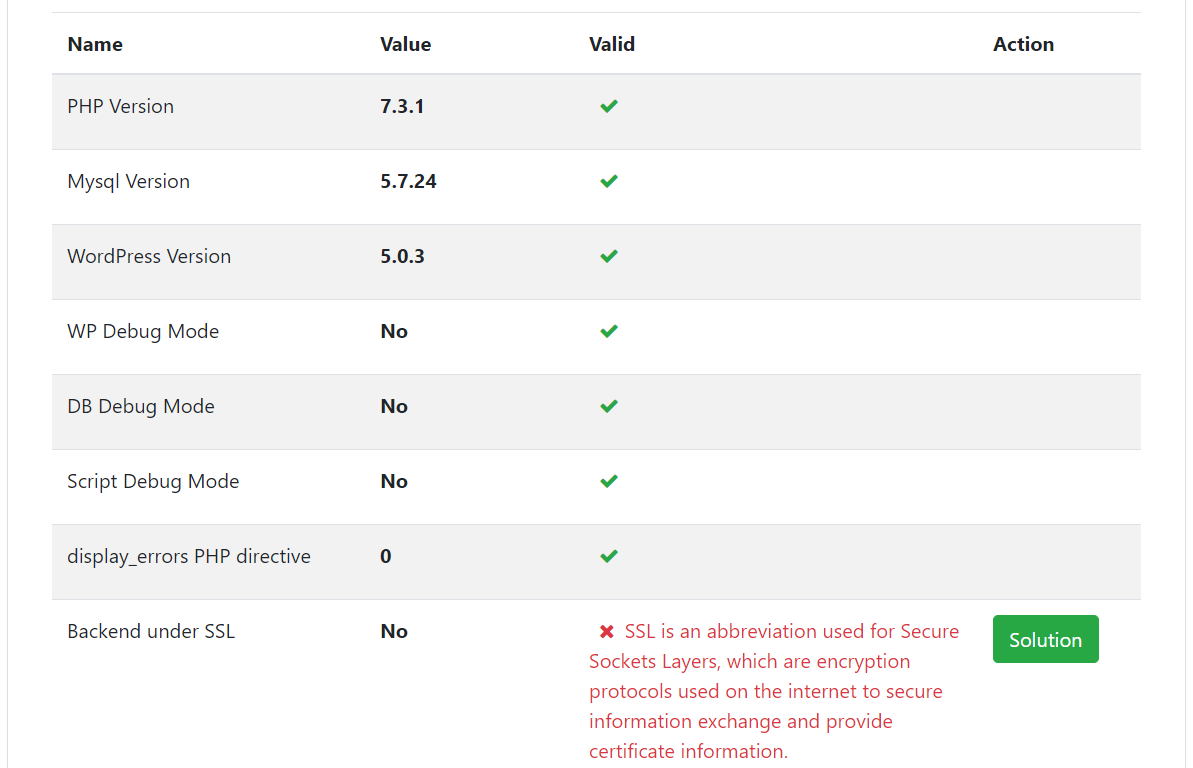
Why is Your WordPress CMS Security Check Important:Most of the casual bloggers start thinking about site security only after they get into first problems and majority of websites get hacked from entirely preventable issues, like not keeping things updated or using insecure passwords. The majority of hacking attempts are made by bots, and you may be able to prevent hacker bots attacks by hiding your WordPress paths: wp-content, wp-include, plugins, themes, etc. Just by changing the main paths, you may be able to protect your website against things like brute-force attacks, SQL-injection, and requests to your PHP files. The test includes checking for updated plugins, themes and different files and functions which are known to hold security breaches.
- 55.9% of vulnerabilities came from plugins.
- Over 90,978 attacks happening per minute on both big and small WordPress sites
- 84% of all security vulnerabilities on the internet are the result of Cross-Site Scripting or XSS attacks.
Is WordPress CMS Vulnerable?:If you like Website Security Check please help us and write us a positive review. https://wordpress.org/support/plugin/website-security-check/reviews/#new-post Try also our security plugin: Hide My Wp Ghost FreeWhat happens if wp-login page is visible:
- WordPress is one of the most popular CMS (Content Management System) options on the Internet these days.
- Around 33% of websites are made with WordPress.
- Even if WordPress is known for being a secure CMS, sometimes hackers do find vulnerabilities. Most site owners don’t know that the biggest risk comes from the installed plugins and themes. You obviously need to be careful with them, as plugin vulnerabilities represented 55.9% of the known entry points reported by respondents.
What happens if WordPress XML-RPC is visible:
- wp-login page is certainly one of the most vulnerable pages on your website.
- If this path is visible means that an authentication path is visible and hackers can perform brute force login attempts.
- A successful brute force attack can give hackers access to your admin area. An unsuccessful one can slow down your website or crush your server.
- There are many strategies for dealing with this problem. The simplest one is to hide WordPress login page.
Why hackers try to access your Wordpress website using xmlrpc.php file?:
- XML-RPC is an API that allows anyone to interact with your WordPress website.
- XML-RPC is also a way to manage your site without having to login manually via the wp-login page.
- Instead of 100 login attempts, the hackers could reduce their login attempts to 10 or less and still try 100 or even thousands of passwords to each request.
- XML-RPC service is always at high risk for WordPress websites. For your safety, you should disable this service.
- By disabling xml-rpc you can protect your website from DDoS attacks, brute force attacks, malicious pingback response.
安装:
Manually install the Website Security Check plugin:
- Log In as an Administrator on your WordPress site.
- In the menu displayed on the left, there is a “Plugins” tab. Click it.
- Now click “Add New”.
- There, you have the “Upload” button. Click the "Upload" button
- Upload the website-security-check.zip file.
- After the upload it’s finished, click Activate Plugin.
- Start checking your website security with one click
- Enjoy! Website Security Check Security WordPress Security Check
屏幕截图:
常见问题:
Does this plugin work on WP Multisite?
Yes, the plugin works on both Single Website and WP Multisite. The plugin also works with Apache, Nginx, IIS and LiteSpeed servers
Is this Plugin free of charge?
Yes. The plugin will always be free. We will include all the required Security updates.
Is this plugin going to protect my website from all hackers?
This plugin will not protect your website from hackers but it will detect the security flaws.
更新日志:
1.2.00
- Compatible with WordPress 5.5
- Fixed some task issues
- Compatible with WordPress 5.4
- Compatible with WordPress 5.3.1
- Added dashboard security meter
- Added new tasks in Security check
- Update the compatibility with more plugins
- Compatible with WordPress 5.3
- Update security tasks
- Compatible with WordPress 5.2.2
- Update compatibility with HTTPS
- Fix minor bugs
- Compatible with WordPress 5.2.1
- Compatible with WordPress 5.2
- Compatible with WordPress 5.1.1
- Compatible with WordPress 5.1
- Update - Uploaded plugin