WPVulnerability
| 开发者 |
closetechnology
davidperez javiercasares lbonomo alexclassroom |
|---|---|
| 更新时间 | 2026年1月20日 23:01 |
| PHP版本: | 5.6 及以上 |
| WordPress版本: | 6.9 |
| 版权: | GPL-3.0-or-later |
| 版权网址: | 版权信息 |
标签
下载
详情介绍:
This plugin integrates with the WPVulnerability API to provide real-time vulnerability assessments for your WordPress core, plugins, themes, PHP version, Apache HTTPD, nginx, MariaDB, MySQL, ImageMagick, curl, memcached, Redis, and SQLite.
It delivers detailed reports directly within your WordPress dashboard, helping you stay aware of potential security risks. Configure the plugin to send periodic notifications about your site's security status, ensuring you remain informed without being overwhelmed. Designed for ease of use, it supports proactive security measures without storing or retrieving any personal data from your site.
Data reliability
The information provided by the information database comes from different sources that have been reviewed by third parties. There is no liability of any kind for the information. Act at your own risk.
安装:
Automatic download
Visit the plugin section in your WordPress, search for [wpvulnerability]; download and install the plugin.
Manual download
Extract the contents of the ZIP and upload the contents to the
/wp-content/plugins/wpvulnerability/ directory. Once uploaded, it will appear in your plugin list.屏幕截图:
常见问题:
Where does the vulnerability information come from?
The origin is in the WPVulnerability.com API. The vulnerabilities that appear in this API come from different sources, such as CVEs.
Is data from my site sent anywhere?
No. Never. Your privacy is very important to us. We do not commercialize with your data.
What vulnerabilities will I find?
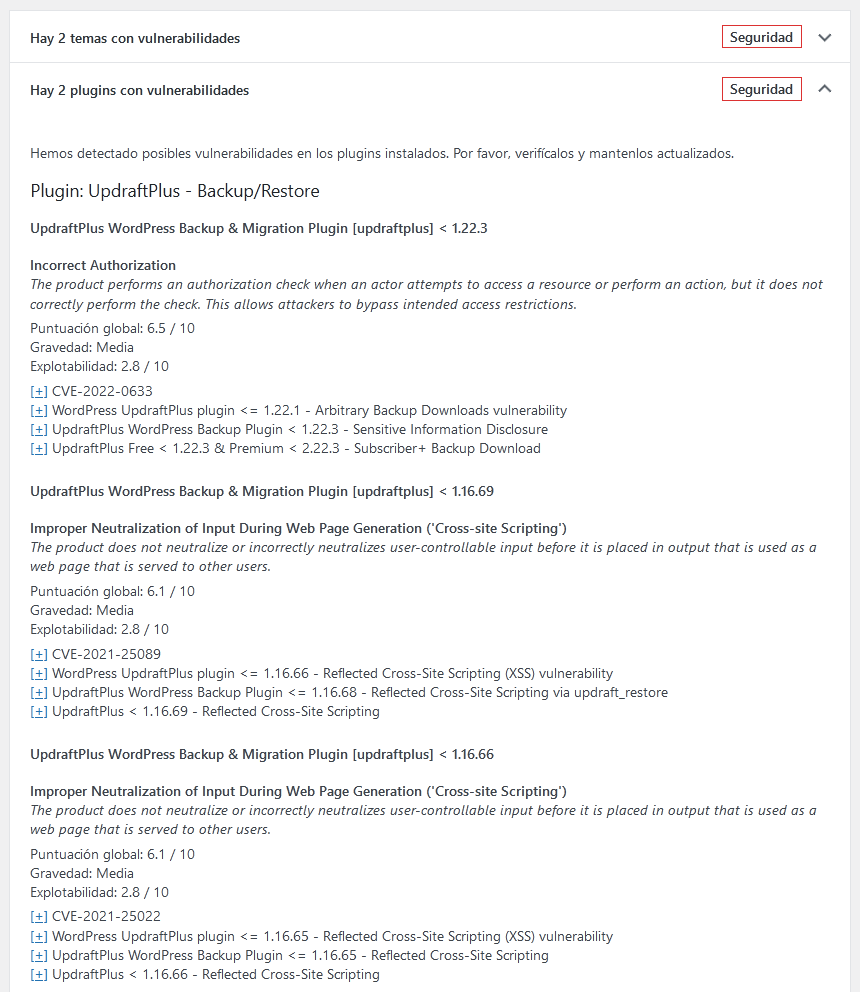
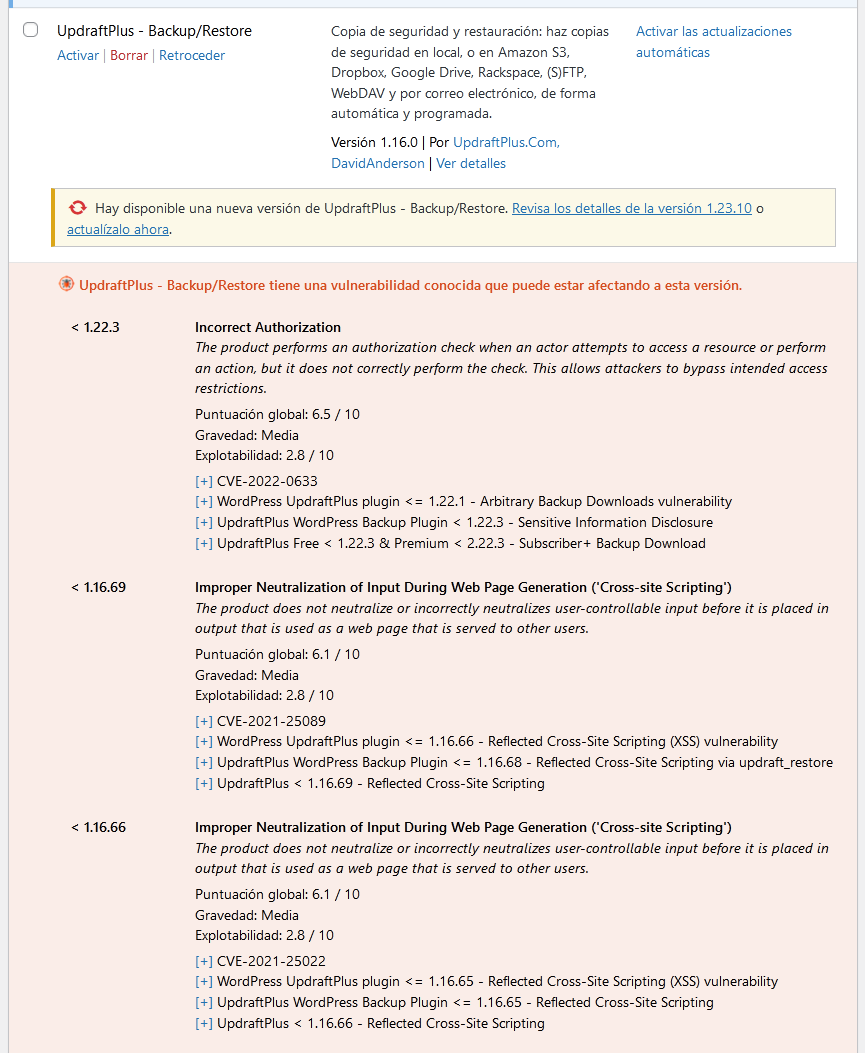
Vulnerabilities in WordPress Core, Plugins, Themes, PHP, Apache HTTPD, nginx, MariaDB, MySQL, ImageMagick, curl, memcached, Redis, and SQLite are documented.
What do I do if my site has a vulnerability?
First of all, peace of mind. Investigate what the vulnerability is and, above all, check that you have the latest version of the compromised element. We actively recommend that you keep all your WordPress and its plugins up to date. Contact your hosting provider to patch non-WordPress vulnerabilities (like web server, databases, and other software).
更新日志:
[4.3.1] - 2026-01-20
Fixed
- Dashboard widget now correctly counts only vulnerabilities from enabled components, excluding disabled ones from settings.
- Status badge calculation (Critical/Warning) now properly considers only enabled components when determining severity level.
- Fixed PHPCS warnings for global variables without plugin prefix in wpvulnerability-admin.php and wpvulnerability-adminms.php.
- WordPress: 4.7 - 6.9
- PHP: 5.6 - 8.5
- WP-CLI: 2.3.0 - 2.11.0
- PHP Coding Standards: 3.13.5
- WordPress Coding Standards: 3.3.0
- Plugin Check (PCP): 1.8.0
- Complete Admin Interface Redesign: Modern card-based layout with visual component cards, improved spacing, color-coded status badges, and responsive grid layouts across all Settings tabs (Security, About, Logs, Tools, Analysis, and Notifications).
- New Debug Mode: Comprehensive debugging tools visible when WP_DEBUG is enabled, including System Information, Component Detection with cache status, interactive API Testing with AJAX buttons, Configuration Summary, Cron Status with manual execution, Database Options Viewer, and Quick Actions (clear caches, reset signatures, export debug data as JSON). Includes enhanced web server detection for 9 different servers.
- Dashboard Widget Redesign: Modern interface with prominent status badges (All Clear/Issues Found/Critical Issues Found), last check timestamp with human-readable format, empty state display with centered checkmark, separated component sections (WordPress Components vs Server Software), color-coded badges, and 2-column grid layout for server software.
- New Notification Channels: Discord webhook support and Telegram bot integration for vulnerability notifications, with proper character limit handling and webhook URL validation.
- Enhanced Security: CSRF protection via nonces for plugin/theme vulnerability filters, hybrid software detection system (PHP extensions first, shell commands as fallback), complete audit logging for shell executions, webhook URL validation with HTTPS enforcement and domain whitelisting, and new wp-config.php security constants.
- Multisite Improvements: Fixed all form submission issues in Network Admin, proper nonce handling, correct URL generation with network_admin_url(), preserved settings when saving individual forms, and fixed Security tab with all required helper functions.
- Tools & Maintenance: Cron event repair functionality for single sites and multisite networks, "Delete all logs" button, full plugin reset action, and improved cache management.
- Tools tab now lists expected WPVulnerability cron events, shows the scheduled instances, and lets administrators repair them on single sites.
- Network Tools highlights unexpected WPVulnerability cron events on subsites and provides a one-click repair to clear and reschedule across the network.
- Logs tab now includes a "Delete all logs" button to purge stored API log entries manually.
- Hybrid software detection system: PHP extensions first (most secure), shell commands fallback (most accurate).
- Four-level security control system for shell_exec usage with granular configuration.
- Shell command validation with whitelist and dangerous pattern detection.
- Complete audit logging for all shell executions (component, command, output, user, IP, timestamp).
- New wp-config.php constants:
WPVULNERABILITY_DISABLE_SHELL_EXEC,WPVULNERABILITY_SECURITY_MODE,WPVULNERABILITY_SHELL_EXEC_WHITELIST. - Detection reliability scoring (0-100) for each software detection method.
- Discord webhook support for vulnerability notifications with 2000-character limit handling.
- Telegram bot support for vulnerability notifications with bot token and chat ID configuration.
- Documentation links for Discord webhook setup (https://support.discord.com/hc/articles/228383668).
- Documentation links for Telegram bot setup (https://core.telegram.org/bots).
- Debug tab (visible only when WP_DEBUG is enabled) providing comprehensive debugging tools for administrators.
- wpvulnerability-debug.php file with 11 helper functions for debug functionality (~18KB).
- Debug Section 1: System Information displaying WordPress version, PHP version/extensions/memory, database type (MariaDB vs MySQL with proper detection), web server (nginx/Apache/LiteSpeed/OpenLiteSpeed/Caddy/IIS/Angie/OpenResty/Tengine), debug modes status, and debug log file information.
- Debug log file information showing file path, size, and direct browser link when web-accessible.
- Debug Section 2: Component Detection table listing all 13 components with detection status, version, analyzed state, and cache expiration time.
- Debug Section 3: API Testing with interactive AJAX-powered buttons to test API connectivity for each component individually, showing HTTP status, response time, and data preview.
- Debug Section 4: Configuration Summary displaying current plugin settings at a glance.
- Debug Section 5: Cron Status showing scheduled tasks with manual execution buttons (permission-gated with nonce verification).
- Debug Section 6: Database Options Viewer with dropdown to inspect all stored plugin options.
- Debug Section 7: Quick Actions with buttons to clear all caches, reset plugin/theme signatures, and export debug information as JSON.
- Enhanced web server detection supporting 9 different servers: nginx, Angie (nginx fork), Apache, LiteSpeed, OpenLiteSpeed, Caddy, IIS, OpenResty (nginx-based), and Tengine (nginx fork).
- Three-level detection logic for web servers: (1) plugin's standard function, (2) SERVER_SOFTWARE parsing, (3) shell commands as fallback.
- Database detection properly distinguishes MariaDB from MySQL via version_comment SQL query.
- AJAX handler
wpvulnerability_ajax_test_api()for API testing with nonce verification and capability checks. - Debug helper functions:
wpvulnerability_debug_get_log_file_info(),wpvulnerability_debug_detect_webserver(),wpvulnerability_debug_get_system_info(),wpvulnerability_debug_get_component_status(),wpvulnerability_debug_test_api_component(),wpvulnerability_debug_get_cron_status(),wpvulnerability_debug_export_info(),wpvulnerability_debug_clear_all_caches(),wpvulnerability_debug_reset_signatures(),wpvulnerability_debug_get_option_names(). - Debug tab POST handlers in both wpvulnerability-admin.php and wpvulnerability-adminms.php with nonce verification for all actions.
- Debug tab render functions in wpvulnerability-admin.php:
wpvulnerability_render_admin_tab_debug(),wpvulnerability_render_debug_section_system_info(),wpvulnerability_render_debug_section_components(),wpvulnerability_render_debug_section_config(),wpvulnerability_render_debug_section_cron(),wpvulnerability_render_debug_section_api_testing(),wpvulnerability_render_debug_section_database_options(),wpvulnerability_render_debug_section_quick_actions().
- Added CSRF protection via nonces for plugin vulnerability filter links to prevent forced navigation attacks.
- Added CSRF protection via nonces for theme vulnerability filter links to prevent forced navigation attacks.
- Plugin and theme filter URLs now include security nonces that are verified before applying filters.
- Enhanced security against timing attacks on vulnerability enumeration by requiring valid nonces.
- Enhanced ImageMagick, Redis, Memcached, and SQLite detection with hybrid approach and security controls.
- All shell commands hardcoded and validated - no user input involved.
- Shell execution wrapper with complete security checks and logging.
- Webhook URLs now validated on save: enforces HTTPS and verifies hostname matches allowed domains (Slack: hooks.slack.com, Teams: office.com/office365.com/api.hooks.microsoft.com, Discord: discord.com/discordapp.com).
- Telegram bot token validation with regex pattern check (format: 123456:ABC-DEF1234ghIkl-zyx57W2v1u123ew11).
- Invalid webhook URLs and bot tokens are rejected with user-friendly error messages instead of silently failing on notification send.
- Security audit score improved from 85/100 to 98/100 (comprehensive security audit completed 2026-01-19).
- Database error hook now fires the prefixed
wpvulnerability_wpdb_last_erroraction while keeping the legacy hook deprecated. - Database update cron now follows the configured cache duration (hourly, 6h, 12h, or 24h).
- Translations load on init to avoid early textdomain warnings.
- Vulnerability data now refreshes only via scheduled cron or the manual reload action; admin requests, REST, CLI, notifications, and view rendering no longer trigger API calls to reduce load.
- Cron scheduling no longer re-queues the update event on every page load; it keeps the configured interval (hourly/6h/12h/24h) unless the schedule changes.
- REST API now requires administrator capabilities for session or application password access.
- Admin reset and test email actions enforce admin capabilities.
- API client timeouts corrected to 2.5 seconds to avoid long hangs.
- Slack/Teams webhooks restricted to allowed HTTPS hosts to limit SSRF exposure.
- Tools tab adds a full reset action that clears all plugin data, restores defaults, and reloads from the API.
- Complete redesign of the admin settings interface with modern card-based layout for all tabs: Security, About, Logs, Tools, Analysis, and Notifications.
- Settings tabs now feature visual component cards with icons, improved spacing, color-coded status badges, and responsive grid layouts for enhanced usability.
- Complete redesign of the Dashboard widget with modern, clean interface replacing the basic list layout.
- Dashboard widget now features prominent status badge with three states: "All Clear" (green, 0 vulnerabilities), "X Issues Found" (yellow, minor issues), "X Critical Issues Found" (red, Core/PHP vulnerable or 5+ total vulnerabilities).
- Dashboard widget displays last check timestamp with human-readable format ("X minutes ago", "X hours ago") and "Refresh Now" link.
- Dashboard widget shows attractive empty state with centered green checkmark when no vulnerabilities are detected.
- Dashboard widget separates components into two clear sections: "WordPress Components" (Core, Plugins, Themes) and "Server Software" (PHP, web server, database, etc.).
- Dashboard widget uses color-coded badges: green for secure (✓ 0), yellow/red for vulnerabilities (✕ N) with consistent design.
- Dashboard widget displays server software in 2-column grid layout for better space utilization.
- Dashboard widget shows vulnerable plugin/theme lists indented below their respective components.
- Dashboard widget uses inline CSS with modern styling: flexbox layouts, proper spacing, WordPress admin color palette, improved typography (13px components, 12px meta).
- Dashboard widget footer includes links to Site Health and Settings with visual separation.
- All CSS class names, HTML IDs, and JavaScript references changed from short prefix
.wpv-to full prefix.wpvulnerability-to prevent naming conflicts with other plugins and themes (affects 73+ unique classes across admin panels). - All inline CSS from admin panels moved to external assets/admin.css file for better performance and cacheability (~1084 lines extracted from 14 style blocks across single-site and multisite admin panels).
- License updated from GPL2+ to GPL3+.
- Saving partial forms (e.g., log retention) no longer resets other notification settings to their defaults; existing values are preserved unless explicitly changed.
- Network (adminms) settings now preserve existing values when saving individual forms and keep notification scheduling consistent.
- Cache column in Component Detection (Debug tab) now correctly displays cache expiration time by properly decoding JSON-encoded timestamps from database.
- Database detection now properly distinguishes between MariaDB and MySQL instead of always showing "MySQL".
- Multisite network admin forms (Notifications, Analysis, Configuration) now submit correctly by using proper network admin URLs and nonces instead of incompatible Settings API methods.
- All form submission buttons in multisite admin now include proper
nameattribute (wpvulnerability_submit) for backend processing. - Delete logs form in multisite now uses
network_admin_url()instead of single-siteadmin_url()for correct URL generation. - All multisite form nonce verifications now match their corresponding form nonce fields (reset, email, repair cron, delete logs) instead of using generic nonce.
- Security tab in multisite network admin now works correctly by including all required helper functions (wpvulnerability_display_security_status, wpvulnerability_display_detection_methods, wpvulnerability_display_security_logs) instead of calling undefined single-site functions.
- Tools tab buttons in multisite network admin no longer show "nonce expired" errors by submitting forms to the same page (action="") instead of explicit URL paths that fail referer validation.
- Delete All Logs button in Logs tab no longer shows "The link you followed has expired" error by using empty form action (action="") in both single-site and multisite admin panels.
- Logs tab pagination now displays horizontally instead of vertically by properly targeting list elements (ul with inline-flex) and individual page links (a and span within li) to work correctly with WordPress paginate_links() 'type' => 'list' output.
- WordPress: 4.7 - 6.9
- PHP: 5.6 - 8.5
- WP-CLI: 2.3.0 - 2.11.0
- PHP Coding Standards: 3.13.5
- WordPress Coding Standards: 3.3.0
- Plugin Check (PCP): 1.8.0
- Fixed authorization vulnerability in REST API endpoints that allowed low-privileged users to access sensitive vulnerability data. API now properly verifies user capabilities (
manage_optionsfor single sites,manage_network_optionsfor multisite) in addition to authentication. - Added direct access protection to wpvulnerability-api.php to prevent direct file execution outside WordPress context.
- WordPress: 4.7 - 6.9
- PHP: 5.6 - 8.4
- WP-CLI: 2.3.0 - 2.11.0
- PHP Coding Standards: 3.13.5
- WordPress Coding Standards: 3.3.0
- Plugin Check (PCP): 1.8.0
- Clear legacy WPVulnerability cron events from multisite subsites so updates and log cleanup only run on the main site.
- WordPress: 4.7 - 6.9
- PHP: 5.6 - 8.4
- WP-CLI: 2.3.0 - 2.11.0
- PHP Coding Standards: 3.13.5
- WordPress Coding Standards: 3.3.0
- Plugin Check (PCP): 1.7.0