WP PGP Encrypted Emails
详情介绍:
README.markdown file for details on cryptographic implementation and API usage.
Donations for this and my other free software plugins make up a chunk of my income. If you continue to enjoy this plugin, please consider making a donation. :) Thank you for your support!
Plugin features:
- Processes all email your site generates, automatically and transparently.
- Configure outbound signing: sign email sent to all recipients, or just savvy ones.
- Per-user encryption keys and certificates; user manages their own OpenPGP keys and S/MIME certificates.
- Compatible with thousands (yes, thousands) of third-party contact form plugins.
- Full interoperability with all standards-compliant OpenPGP and S/MIME implementations.
- Options to enforce further privacy best practices (e.g., removing
Subjectlines). - Fully multisite compatible, out of the box. No additional configuration for large networks!
- No binaries to install or configure; everything you need is in the plugin itself.
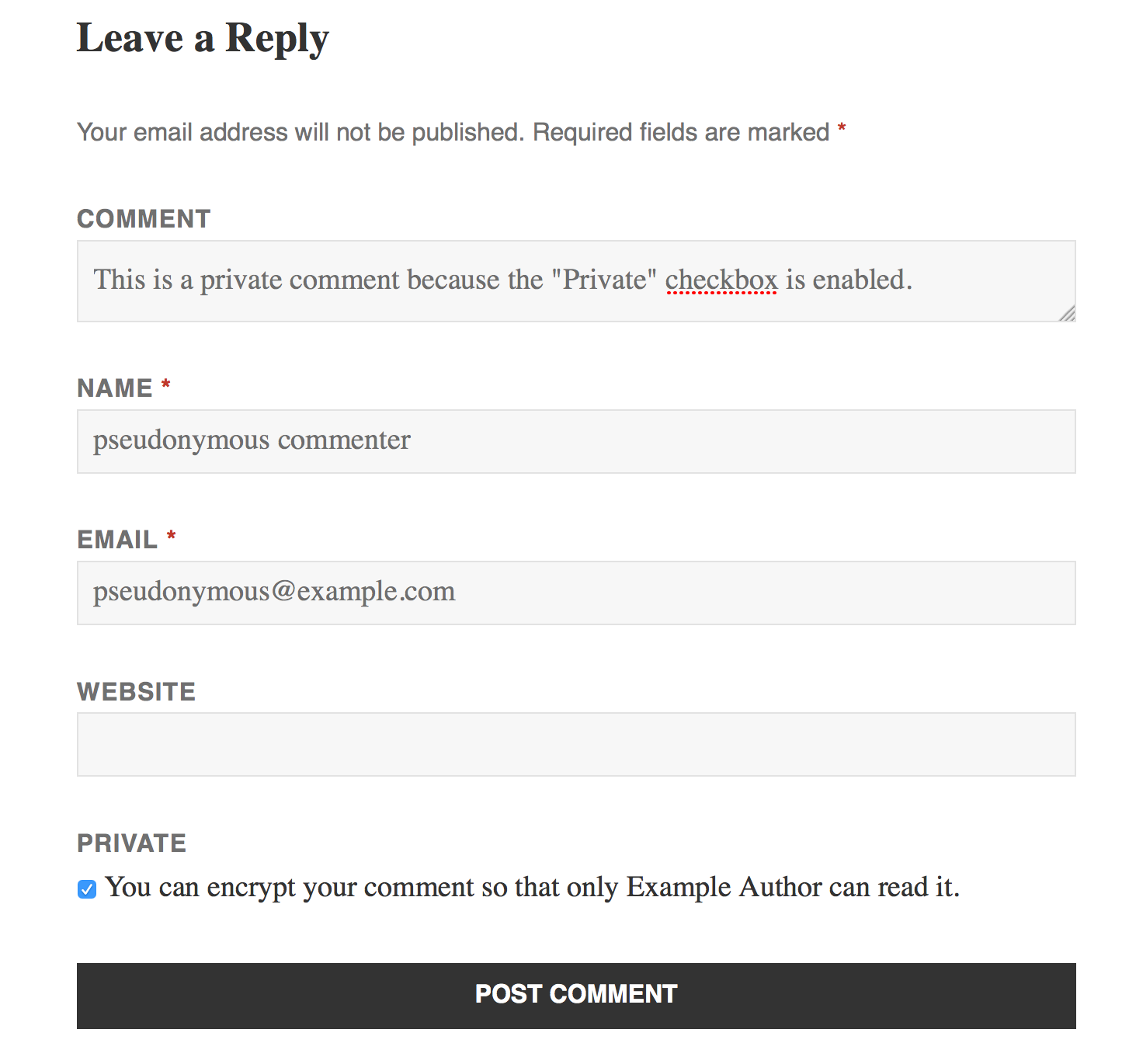
- Bells and whistles included! For instance, visitors can encrypt comments on posts so only the author can read them.
- Built-in, customizable integration with popular third-party plugins, such as WooCommerce.
- Always FREE. Replaces paid email encryption "upgrades," and gets rid of yearly subscription fees. (Donations appreciated!)
- And more, of course. ;)
- The Electronic Frontier Foundation's Surveillance Self-Defense guide to PGP
- RiseUp.net's OpenPGP best practices guide
- OpenPGP.org
安装:
- PHP version 5.4 or later.
- S/MIME support requires the OpenSSL PHP extension. (This is almost certainly already installed for you.)
- Download the latest plugin code from the WordPress plugin repository.
- Upload the unzipped
wp-pgp-encrypted-emailsfolder to the/wp-content/plugins/directory of your WordPress installation. - Activate the plugin through the "Plugins" menu in WordPress.
- The Electronic Frontier Foundation's Surveillance Self-Defense guide to PGP
- RiseUp.net's OpenPGP best practices guide
- Jerzy Gangi's "Best PGP Tutorial for Mac OS X, ever"
- DeepDotWeb's Basic Guide to PGP on Linux
- BitCoin Not Bombs: Beginner's Guide to PGP
屏幕截图:
其他记录:
- To link to a site's OpenPGP signing public key:
<?php print admin_url( 'admin-ajax.php?action=download_pgp_signing_public_key' ); ?>
常见问题:
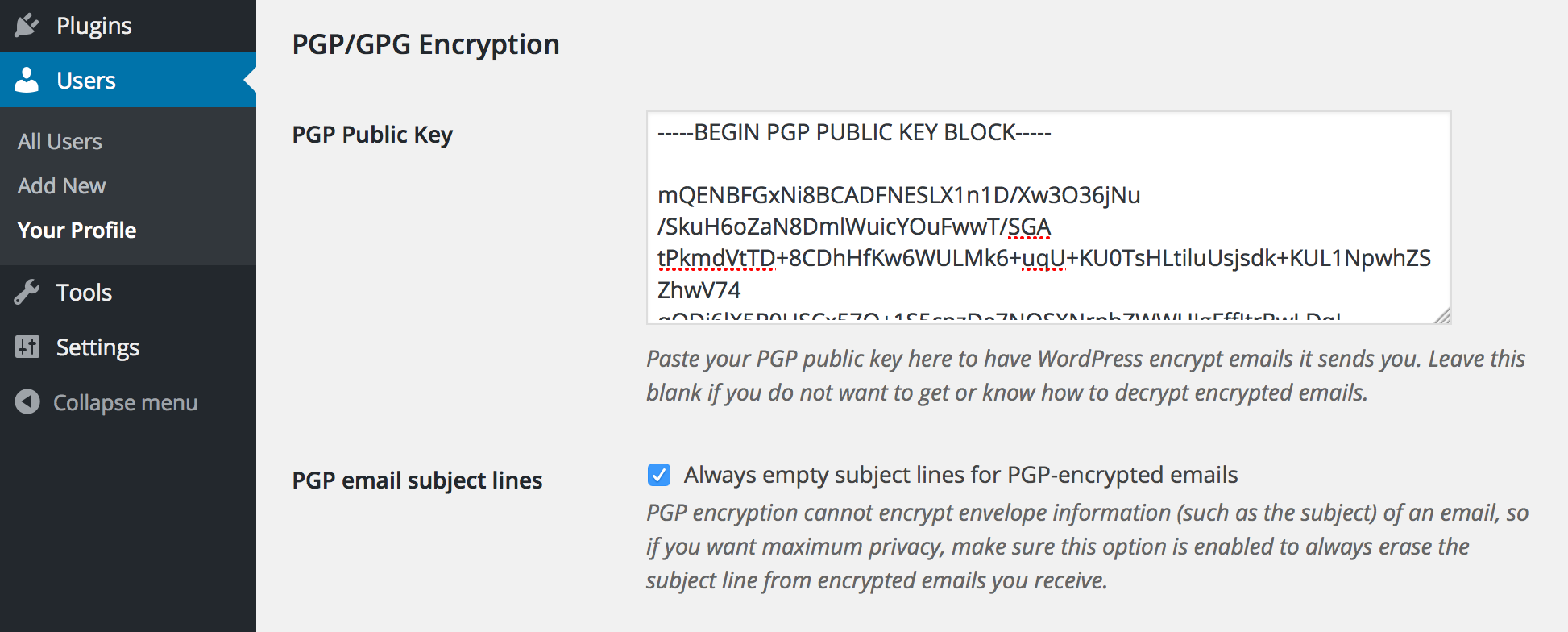
What is an OpenPGP-compatible client and where can I get one?
An OpenPGP-compatible client is simply an app that can read, write, and verify messages encrypted or signed using PGP technology. There are great, free apps for every major platform, including Windows, Mac, Linux, Android, iPhones, iPads, and more. Which app you choose depends largely on which device you already have, and then a bit about your personal tastes. Since there are so many OpenPGP-compatible apps to choose from, I recommend sticking to the ones listed on the PRISM-Break.org website. (Note that PRISM-Break calls it "GPG" instead of "PGP," but the two terms are generally synonymous.) Once you choose an OpenPGP-compatible app for your platform, consider seeking out its help and support documentation to get started using it, or check out some of the generic PGP/GPG guides listed at the end of this plugin's Installation page.
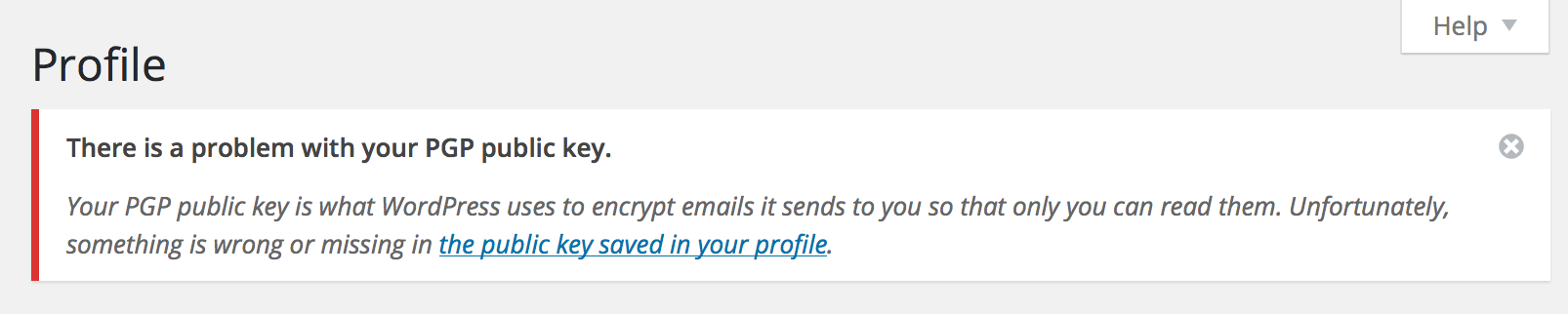
I can't decrypt messages addressed to my admin email address!
If you have registered a WordPress user account with the same email address as your site's admin email address (in the Settings → General screen), then WP PGP Encrypted Emails will first check for a public key or certificate in the administrative Email Encryption settings (Settings → Email Encryption) before looking at your user's profile settings. If an encryption key or certificate exists in the administrative settings, that key will be used instead of the key or certificate in the user's profile. To resolve this issue, either ensure that you enter encryption keys in only one location (the administrative screen or the user's profile), or ensure these keys are the same. If you still cannot decrypt messages, make absolutely certain you have the matching private key or certificate corresponding to the public key or certificate that was used to encrypt the message. Unfortunately, it is highly infeasible that anyone on Earth will be able to decrypt messages encrypted to a public key or certificate that you do not have the associated private key for. That is, of course, the whole point of this software.
How do I read an encrypted comment?
If you have received a "Private" comment, you will need to use an OpenPGP-compatible PGP client to decrypt and read it. There are many free apps that do this. Which one you choose depends on what kind of computer you are already using. If you use Windows, I suggest installing and using GPG4Win since it provides the most features. For Mac OS X users, I suggest MacGPG for the same reason, and Linux users should check their distro's package repository for compatible options. (For Ubuntu users, the Seahorse-Nautilus plugin is popular.) I might also add support for an in-browser client based on OpenPGP.js at some point, but for now you will still need an external program to read encrypted comments. Please consider donating to help resource me work on this if that is a feature you'd like to see.
Why are emails from [other-plugin-here] not being encrypted?
Make sure the emails the other plugin sends are being addressed to an email account that WordPress knows about and that WordPress knows which OpenPGP public key or S/MIME certificate to use when encrypting email destined for that address.
More specifically, this means the TO: field of the outgoing email needs to match either your WordPress's "admin email" address or the email address of one of your WordPress user accounts, and you need to provide the OpenPGP public key or S/MIME public certificate you want WordPress to use when encrypting the message and sending email to that address. In many contact form plugins, you can supply an arbitrary email address to send those emails to, but if that email address is not the address of a user on your site, WP PGP Encrypted Emails won't know which OpenPGP public key or S/MIME public certificate to use for encryption.
As a workaround, simply create an unprivileged ("Subscriber" role) new WordPress user account with that email address and enter the OpenPGP public key or S/MIME certificate in that user's profile. (Either accept the automatically generated password, or supply a new very strong passphrase, since you will not need to remember it because you will never need to log in with that user account.)
Why are my emails appearing strangely in my email client?
Issues with character sets, accented characters, different human languages, or content types not appearing correctly are almost always the result of a misconfiguration in the email-sending plugin you are using. Many contact form plugins, for example, allow you to supply custom email headers. WP PGP Encrypted Emails takes great care not to corrupt the email message sent by the underlying plugin that generated the email in the first place. However, this also means that if you do not set up your contact form or email-sending plugin correctly, this plugin won't fix the error. Most often, this is simply a matter of setting the correct Content-Type header in your contact form or email-sending plugin's settings.
Is this plugin really secure?
Against the NSA? No, probably not. Against a nosy co-worker? Yes, probably. The "realness" of security cannot "really" be measured in abstract, imprecise terms, but rather only based on what real threats you are likely to face and what risks you are vulnerable to if those threats materialize in reality. You have a much better sense of the answers to these things than I do for your situation, because I am not you. Security professionals call this process "threat modeling," and if you are "really" concerned for your security (I encourage you to be!) then learning how to conduct a threat assessment for yourself is a good idea. Learn more about threat modeling from the EFF's Surveillance Self-Defense Guide.
If this plugin isn't secure against the NSA, what good is it?
TL;DR: Don't let perfect be the enemy of good. First of all, not everyone's security needs are the same. (See "threat modeling," discussed in the previous question.)
- Against an opportunistic attacker, your security measures merely need to be better than your neighbor's in order to be sufficient to deter attacks. This is "good enough" security for most users of WordPress, especially on shared hosting accounts (which are generally closer to the unsafe side of the security spectrum no matter what plugins you install anyway).
- Against a well-resourced, determined adversary who has specifically singled you out, however, what matters is that your ability to secure yourself exceeds your adversary's ability to compromise the specific security precautions you've put in place. Your relative security as compared with your neighbor's doesn't matter. In this case, it is better to do anything and everything you reasonably can do for your protection, even if no specific security measure will be enough on its own. This is known as "defense in depth" and is analogous to the way a medival castle had a moat that surrounded an outer wall which itself surrounded an inner wall protecting a keep. These concentric rings of security provide redundancy and serve to slow an attacker's intrusion. This plugin can be considered one small part of a larger defense-in-depth security approach for your website.
Can I use a "strong" key for my user account?
Yes. You can use any OpenPGP public key you generate from any OpenPGP-compatible client.
How strong is the signing key the plugin generates?
When generating an OpenPGP signing keypair for your WordPress site, this plugin will create a 2,048-bit RSA OpenPGP keypair. This is considered "okay" (but not "great") by 2018 standards. Unfortunately, many hosts will not allow the plugin to create a stronger keypair because of the computation required. Then again, this key is used only for signing, not encryption. Your own OpenPGP public key is always used for encryption, and you are of course encouraged to make that key as strong as you want. If you want to use a stronger signing keypair, you can generate one yourself (offline), though you will need to load the key into your WordPress database yourself to use it with this plugin. I consider this extra step "paranoid," but you are of course welcome to be as careful as you feel is appropriate. :)
更新日志:
- Maintenance: Drop support for PHP versions earlier than 7.4, add experimental support for PHP 8.x.
- Maintenance: Update dependencies.
phpseclibis updated to version 2.0.31 and addresses a moderate severity security vulnerability.
- Maintenance: Update dependencies. Note also that this version officially drops support for PHP versions earlier than the current WordPress recommendations, which at the time of this writing is PHP v7.4. If you are still running WordPress in a "legacy" environment (using PHP 5.x), you must update or push your hosting provider to update your version of PHP to 7.4 or greater to continue using this plugin.
- Security: Always use the AES-256 cipher in CBC mode when encrypting S/MIME emails. This change drops support for PHP versions less than 5.4.
- Security: Improved shredding of temporary files needed for S/MIME encryption with 3-pass overwrite and explicit filesystem write buffer flushing.
- Enhancement: Improve S/MIME compatibility with some email clients, notably Roundcube. Props @githubuserx.
- Bugfix: Conflict where admin email without encryption keys matching user email no longer results in unencrypted email being sent.
- Minor code cleanup and documentation improvements.
- Bugfix: Messages with
Content-Type: text/htmlheaders that were also S/MIME encrypted now render properly. Props @githubuserx. - Bugfix: Ensure MIME subtypes in
Content-Typemail headers are retained. - Bugfix: Do not enqueue admin-area stylesheet on site front-end.
- Bugfix: Fixes a problem where S/MIME email sending fails due to a web hoster restriction.
- Enhancement: Offer a simple "Send me a test email" button to let inexperienced users easily test their encryption setup.
- Feature: WooCommerce integration. Customers can add their own OpenPGP keys or S/MIME certificates on their "My Account" front-end supplied by WooCommerce. By default, emails sent to Customers are not signed with the site's PGP signing key, though individual customers can opt-in to receive either encrypted and signed or just signed emails as they wish.
- Developer: Theme authors can override the plugin's default WooCommerce integration file by adding a
woocommerce-functions.phpfile to their theme. Please only do this if you know what you are doing. - Update OpenPGP-PHP libraries to current released version.
- Bugfix: Fix compatiblity with third-party contact form plugins (namely Contact Form 7).
- Bugfix: Fix issue with uninstallation.
- Feature: New S/MIME API filter,
smime_pem_to_der. - This supports certain applications that need certificate data in DER format.
- Bugfix: Fix comment filter call.
- Feature: S/MIME support! :)
- Three new API filter hooks are provided to offer S/MIME encryption. These are
smime_certificate,smime_certificate_pem_encodeandsmime_encrypt. See S/MIME API for details.
- Feature: Configure whether email destined for addresses that are not associated with user accounts are automatically PGP-signed.
- Feature: A "delete PGP signing keypair on uninstall" option has been added. When enabled and the plugin is uninstalled, the site's PGP signing keypair is deleted from the WordPress database.
- Minor bugfixes.
- Bugfix: Generate signing key that can be used to create a revocation certificate.
- Site signing key is generated with correct OpenPGP key flags (shown as
Sfor signing andCfor certification in GnuPG). - Update
openpgp-phplibrary and dependencies.
- Bugfix: Improve compatibility with some third-party plugins.
- Bugfix: Plugins that call
wp_mail()with an array no longer cause PHP warnings. - Bugfix: Fix syntax error when running on PHP 5.3 or earlier.
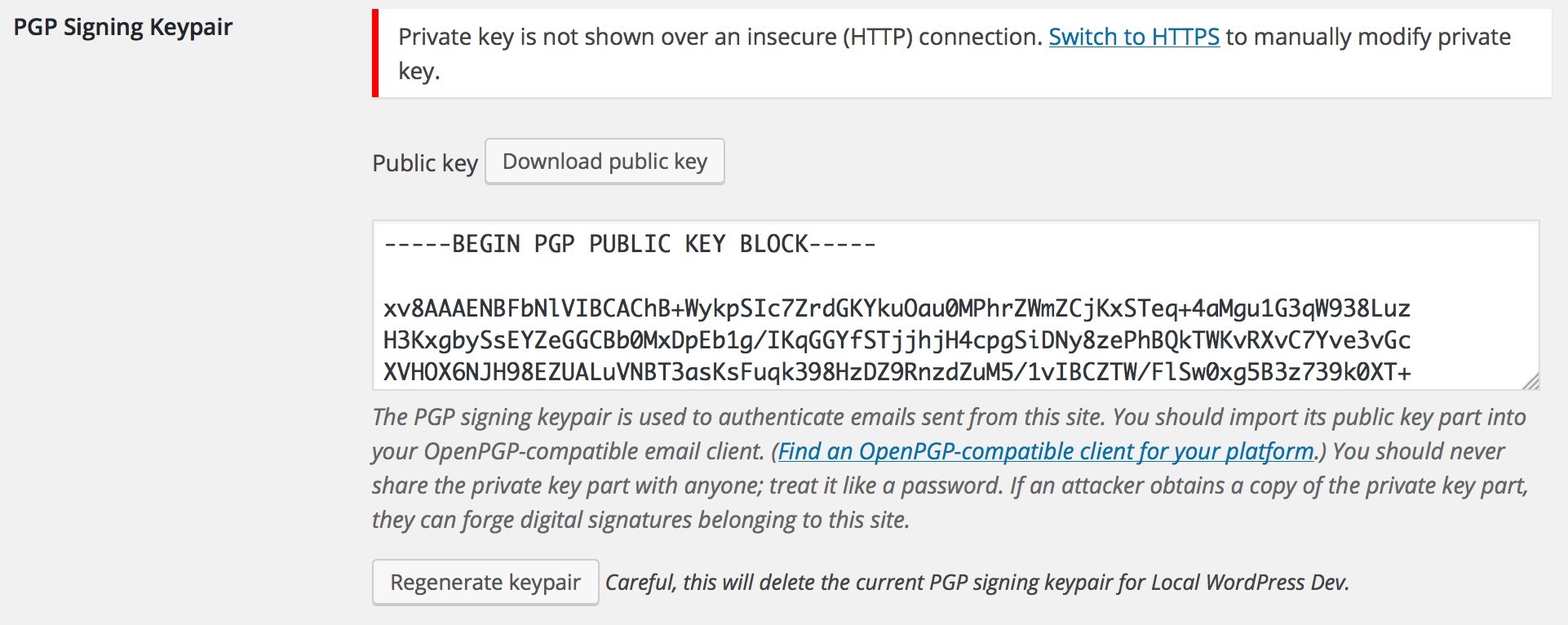
- Feature: Admins can now generate a PGP signing keypair for the blog itself. If a signing keypair exists, outgoing emails will be automatically signed.
- This keypair is intended only for signing outgoing emails from WordPress itself. It is not intended to be used for any other purpose. Do not use this keypair for emails you send from your own mail client. Do not use this keypair as your personal PGP key. Do not export this key for use in any other system. This keypair should be treated as a low-trust, single-purpose keypair reserved exclusively for your website itself.
- After adding a PGP signing keypair, users can download the site's public key part from their profile pages.
- Theme authors can always link to a site's PGP signing public key with the following code:
print admin_url('admin-ajax.php?action=download_pgp_signing_public_key') - Developer: New filter hooks. These are documented on the Other Notes page.
openpgp_enarmorfilter for ASCII-armoring arbitrary OpenPGP data.openpgp_signfilter for (clear)signing an arbitrary message.
- Feature: Authors with a PGP public key set in their profile can now receive "private" comments. Readers write their comment as normal, and can then enable the "Private" checkbox next to the comment submit button. This will automatically encrypt the comment to the post author's PGP public key and saves the comment in the WordPress database as an ASCII-armored string.
- This feature is not secure against eavesdropping, other network attackers, or malicious web host. It does not prevent server administrators from reading the contents of your comment. Rather, it prevents other readers or unprivileged users of the blog from reading your comment after it has been sent to the author. This is useful if, for instance, you want to communicate semi-privately with the author in an otherwise public forum (the comment thread) but do not know the author's email address, perhaps because the author themselves wish to remain pseudonymous (and thus do not provide a valid email address associated with their PGP key).
- Developer: Added two new filters,
openpgp_keyandopenpgp_encryptso plugin developers and theme authors can encrypt arbitrary data, too.
- Security: Switch PGP library to OpenPGP-PGP.
- Bugfix: Fix
Fatal errorin cases where the public key is set tofalse.
- Initial release.